
Experimental Security Analysis of the
App Model in Business Collaboration Platforms
Yunang Chen*, Yue Gao*, Nick Ceccio,
Rahul Chatterjee, Kassem Fawaz, Earlence Fernandes
+
University of Wisconsin–Madison, University of California San Diego
* Equal contribution
+
Work done while at UW-Madison
The 31
st
USENIX Security Symposium, 2022
Boston, MA, USA

1
Business Collaboration Platforms (BCPs)
• Productivity & Team Collaboration
• Third-Party Integrations (Apps)
Figures from slack.com and support.microsoft.com

2
BCPs Have Become A Hub for Sensitive Resources
• Zoom Calls
• DropBox File Sharing
• Email Forwarding
• Code Repository Management
• …
Figure from slack.com
What if the apps are malicious?
Can BCPs enforce security correctly?

3
BCP User
BCP Client
BCP Server Cloud BCP Apps
2. API Calls
5. Response
Background: App Workflow
3. Notification
4. API Calls
1. Interact
“Zoom, start a meeting.”
Message API
User posted a message…
Video Call API: zoom linkRender video call…

4
Background: App Installation
1. App Requests Permissions
2. Read Permission Scopes
– Read user identity
– Read public messages
3. Write Permission Scopes
– Post messages
– Post messages on behalf of users
4. User Approves Permissions
5
Threat Model: Malicious Apps in BCP
Target BCP Workspace
Malicious App
Benign Apps
install
Benign Users
• Attacker tricks the user to
install a malicious app
• The user is curious and
installs a malicious app
• The benign app becomes
malicious

6
Challenges & Our Methodology
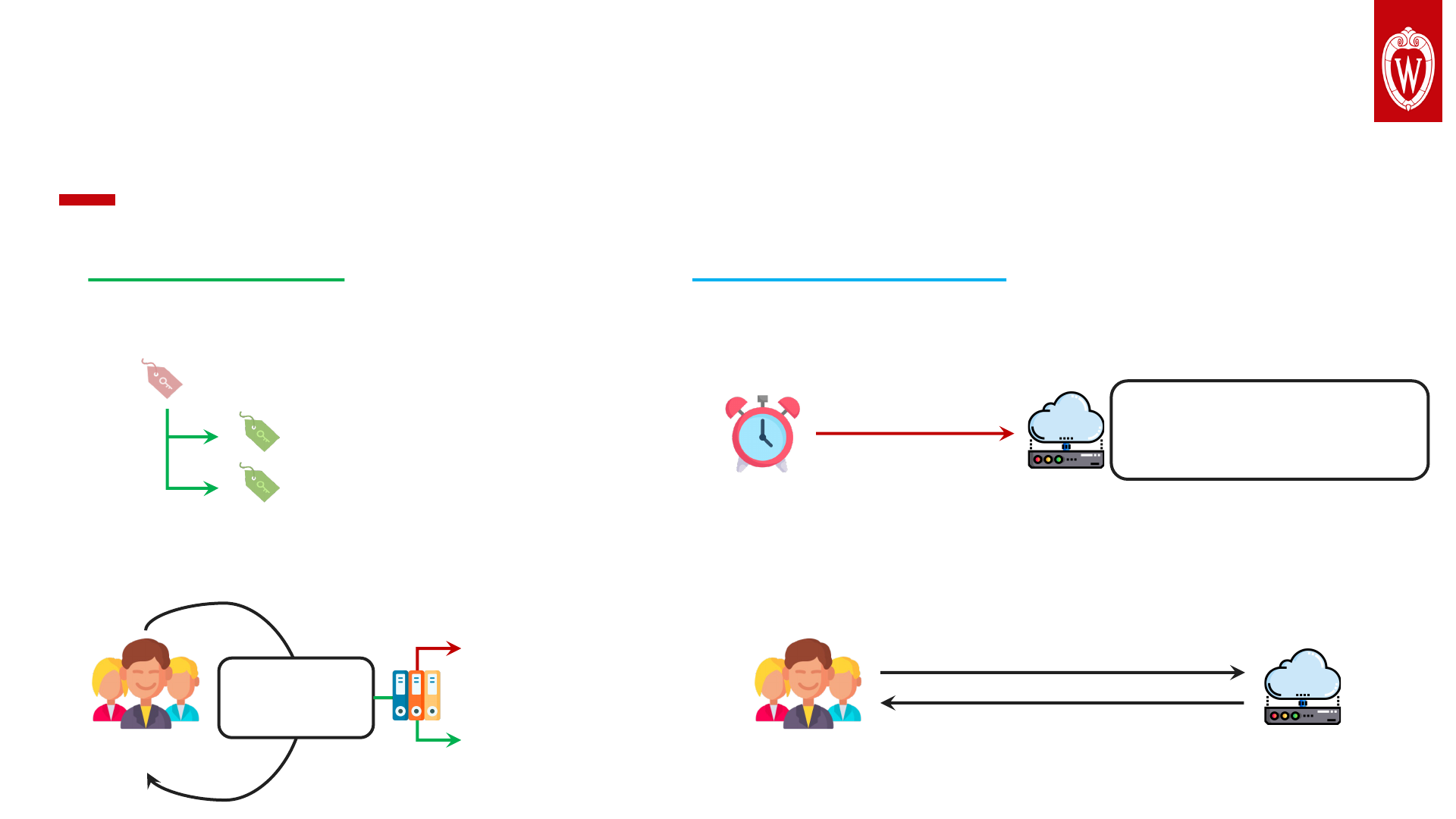
• Incomplete permission model description.
We extract a unified abstraction.
• Closed-source apps in the cloud.
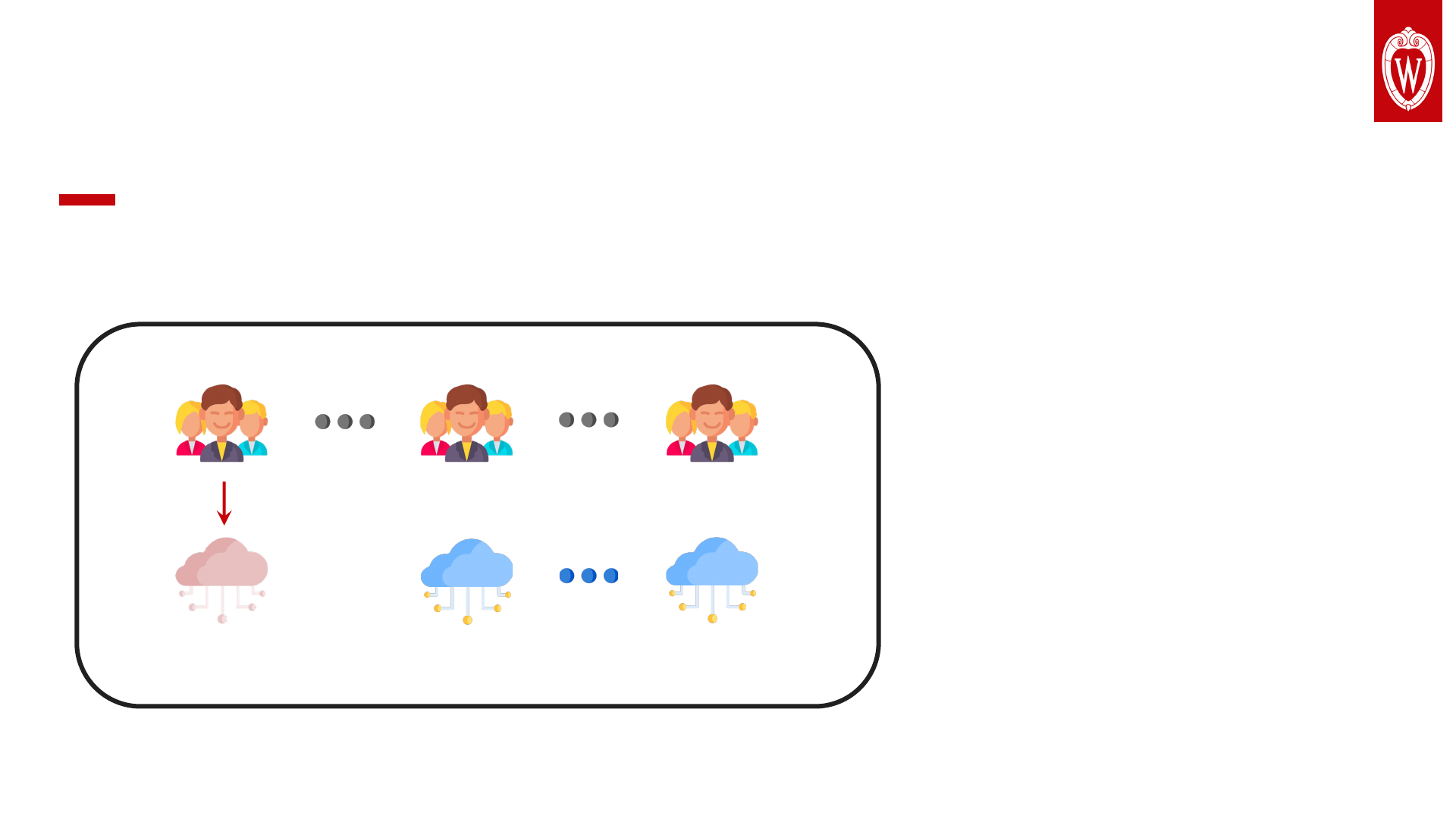
We examine all possible interactions.
• Unscalable in-depth analysis.
We estimate potential attackers & victims.
user-app
app-app
app-user
one permission model
interact
potential attackers / victims

7
A Two-Level Unified Permission Model
• Level 1: coarse-grained OAuth permissions scopes
Resource Group: Private Channels
Channel #3Channel #2Channel #1
BCP App
“read private channel messages”

8
A Two-Level Unified Permission Model
• Level 1: coarse-grained OAuth permissions scopes
• Level 2: fine-grained runtime policy checks
BCP App
“read private channel messages”
Resource Group: Private Channels
Channel #3Channel #2Channel #1
“ refers to private channel #1”

9
Violation of Security Principles
• Least Privilege
Runtime policies are ad-hoc and incomplete.
• Complete Mediation
Provenance of resources are not properly tracked.
“post messages to channels” “post messages to users”
“only if the app joined this channel” null
delegate message
“command”
“command”
user “command”

10
• App-to-App Interaction ➔ Delegation Attacks
• User-to-App Interaction
➔
Command Hijacking
• App-to-User Interaction
➔
Privilege Escalation
All Types of Interactions Are Vulnerable
Post scheduled
message as me
Talk to apps as user
Type “/zoom” to
start a meeting
(also register “/zoom”)
Hijack
“read direct message”
“post message as me”
“read private channels
including other users”

11
Delegation Attack: Merge Malicious PRs
• Step 1: User installed Bitbucket app.
“Merge #1”
“Confirm merge #1?”
“Yes”
“Merged!”

12
Delegation Attack: Merge Malicious PRs
• Step 2: User installed “Send Later” app (our malicious demo).
“Write as User”
Permission

13
Delegation Attack: Merge Malicious PRs
• Step 3: Attacker creates a malicious Pull Request #1.
Bump version to …

14
Delegation Attack: Merge Malicious PRs
• Step 4: Malicious “Send Later” app talks to the Bitbucket app.
First request “merge #1”
Confirm “merge #1”
“Pull request was successfully merged.”

15
Delegation Attack: Merge Malicious PRs
• Step 5: Bitbucket merges the malicious pull request.

16
Potential Prevalence Analysis
• Collect each app’s requested permissions.
• Capable Apps — Have write permissions needed for attacks.
• Susceptible Apps — Have read permissions affected by attacks.
Attacks
# Capable Apps
(MS Teams)
# Capable Apps
(Slack)
# Susceptible Apps
(Slack)
Delegation Attacks 427 (33%) 563 (23%) 1,493 (61%)
Command Hijacking 77 (6%) 270 (11%) 1,266 (52%)
Privilege Escalation n/a 11 n/a
17
Countermeasures: Improve Permission Models
Better Design
– Finer-grained Scopes
– Stricter Runtime Policies
Better Execution
– Track Provenance of Actions
– Explicit User Confirmation
“… to apps”
“post messages as user”
“… to non-apps”
Message
from B
User A
“check if apps
can read A”
“check if apps
can read A & B”
Content: message
From: User (via App)
user: message
Start meeting “/zoom”
“Zoom #1 or Zoom #2 ?”

18
Disclosure & Responses
• Confirmed attacks
• Workspace ➔ a trusted environment
• Administrator ➔ will correctly manage apps
• Our tips for administrators
• Consider limiting users from installing apps
• Actively monitor the behavior of installed apps
• Only approve delegation permissions from trusted apps

19
Summary
Paper Demo
• BCPs have become a hub for sensitive third-party resources.
• We provide security analysis under malicious apps.
• All types of interactions are vulnerable & potentially prevalent.
Command
Hijacking
Delegation
Attack
Privilege
Escalation
