
Endpoint Privilege Management for
Mac
24.4 Administration Guide
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC:6/28/2024

Table of Contents
Endpoint Privilege Management for Mac Administration 8
Achieve Least Privilege on Mac 8
Empower Users and Gain Control 8
Unlock Privileged Activity 8
Take a Pragmatic Approach with Broad Rules 8
Achieve Compliance 8
Apply Corporate Branding 8
Customizable Messaging 9
Simple, Familiar Policy Design 9
Install the Endpoint Privilege Management Policy Editor 10
Install the Endpoint Privilege Management for Mac Client 11
Requirements 11
Install Endpoint Privilege Management for Mac 11
Different Versions of Agents 11
Configure MacOS System Settings 11
Use Anti-tamper Protection 12
Turn on Anti-tamper Protection 13
Turn off Anti-tamper Protection 13
Confirm the Status of the Tool 13
Upgrade the Endpoint Privilege Management Mac Client 13
Uninstall Endpoint Privilege Management for Mac 14
Uninstall Endpoint Privilege Management 14
Uninstall the Mac Adapter 14
Remove the Endpoint Privilege Management Policy 14
Launch the Endpoint Privilege Management Policy Editor 15
Navigate the Endpoint Privilege Management Policy Editor 15
Automatic Save 15
Policies and Templates 17
Users 17
Policies 17
Edit Group Policy 17
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
2
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
This page needed for table of
contents. Do not delete.

Privilege Management Settings 18
Create 18
Delete 18
Export 18
Import 18
Import Template 19
Save Report 19
Set Challenge/Response Shared Key 19
Show Hidden Groups 19
View 19
License 19
Insert a License 19
Endpoint Privilege Management for Mac Response Code Generator 21
Templates 22
macOS QuickStart 22
QuickStart Policy Summary 23
macOS Workstyles 23
macOS Workstyle Parameters 24
macOS Application Groups 25
macOS Messages 25
Customize the QuickStart Policy 26
Mac Specific 27
Multiple Mac Policies 27
Mac Application Templates 27
Add Endpoint Privilege Management for Mac Settings to a Mac Client Computer 27
Mac Sudo Command Arguments Not Supported 28
Use Centrify 28
Third Party Licensing Information 29
Configure Caching on Policies 31
Overview 31
Specifications 31
Configure Caching 31
Change the User Interface 31
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
3
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
This page needed for table of
contents. Do not delete.

Turn on Legacy UI 31
Turn off Legacy UI 32
Policies 33
Workstyles 34
Workstyle Wizard 34
Create Workstyles 36
Disable or Enable Workstyles 37
Workstyle Precedence 37
Workstyle Summary 38
Overview 38
Application Rules 38
Filters 39
Application Groups 41
Create Application Groups 41
View or Edit the Properties of an Application Group 41
Delete an Application Group 41
Duplicate an Application Group 41
Rule Precedence 42
Application Definitions 43
Application Requests Authorization 43
Command Line Arguments 44
File or Folder Name Matches 44
File Hash (SHA-1 Fingerprint) 45
Changes to File Hash Auditing 46
Changes to File Hash Matching Criteria 46
How to Determine a File’s Hash for Matching Criteria 46
File Hash (SHA-256) Matches 47
How to Determine a File’s Hash for Matching Criteria 47
File Version Matches 47
Parent Process Matches 47
Publisher Matches 48
Source 49
URI 49
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
4
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
This page needed for table of
contents. Do not delete.

Install Action Matches 50
Delete Action Matches 50
Manage Disk Mounted Images 51
Configure the defendpoint.plist File 51
Format of Messages 51
Manage System Applications 54
Manage the Endpoint Privilege Management Finder Extension 54
Allow Authorization of the Console Application 55
Configure the Authorization 55
Insert a Binary 57
Insert a Bundle 58
Insert a Package 59
Insert a Script 60
Install Homebrew 60
Allow Standard Users to Install Homebrew vian Endpoint Privilege Management for Mac 61
Insert a Sudo Command 63
Sudo Switches 63
Edit -e Switch 64
Insert a System Preference Pane 65
Add a System Preference Pane 65
Insert Applications from Templates 66
Use the Add Apps to Template Menu 66
Messages 67
Create Messages 68
Multi-factor Authentication using an Identity Provider 69
Authentication and Authorization Groupings in Endpoint Privilege Management 69
Workflow 70
Add an Identity Provider 70
Add the Endpoint Privilege Management Application to Microsoft, Okta, or Ping Identity 71
Create an App Registration 71
Add Endpoint Privilege Management to Okta 73
Add Endpoint Privilege Management to Ping Identity 73
Message Name and Description 75
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
5
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
This page needed for table of
contents. Do not delete.

Message Design 76
Message Header Settings 76
User Reason Settings 77
Authentication and Authorization Settings 77
Sudo User Authorization 79
Image Manager 79
Message Text 81
General 81
Publisher 81
User Reason 81
User Authentication 81
Challenge / Response Authorization 82
Buttons 82
Challenge / Response Authorization 83
Shared Key 83
Generate a Response Code 83
Use Touch ID Authentication with Allow Messages 85
Mac Deployment 86
Add Endpoint Privilege Management for Mac Settings to a Mac Client Computer 86
Mac Policy Structure and Precedence 86
Structure 86
Precedence 87
Audits and Reports 88
Events 88
Use Smart Card Authentication 89
Predeployment Setup 89
Configure Endpoint Privilege Management for Mac Messaging 89
MFA Support in Endpoint Privilege Management for Mac sudo Rules 90
ServiceNow User Request Integration 91
Logging 92
Set up Audit Logs 92
View Unified Logging 93
Obtain Debug Logs from the Endpoint 94
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
6
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
This page needed for table of
contents. Do not delete.

Apply Anonymous Logging to Events 95
Troubleshoot 96
Check Endpoint Privilege Management for Mac is Installed and Functioning 96
Check Settings are Deployed 96
Check Endpoint Privilege Management for Mac is Licensed 96
Check Workstyle Precedence 96
Install macOS Updates On Apple Silicon Hardware 97
Apple Changes with Apple Silicon Hardware 97
Apple-Recommended Method for Updating macOS Devices 97
User-Initiated Software Updates 97
Full Installer or Delta Installer 98
Allow Standard Users to Use the Full macOS Installer via Endpoint Privilege Management
for Mac 101
Supported Method for Full Installer 101
Windows and macOS OS Technical Support Statement 104
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
7
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
This page needed for table of
contents. Do not delete.

Endpoint Privilege Management for Mac Administration
Endpoint Privilege Management for Mac combines privilege management and application control technology in a single lightweight agent.
This scalable solution allows global organizations to eliminate admin rights across the entire business.
Actionable intelligence is provided by an enterprise class reporting solution with endpoint analysis, dashboards, and trend data for
auditing and compliance.
Achieve Least Privilege on Mac
There are many functions that require an admin account to run. While most Mac users typically use an admin account to gain the flexibility
they need, this represents a large security risk in the enterprise. Endpoint Privilege Management for Mac allows users to log in with
standard user accounts without compromising productivity or performance, by allowing the execution of approved tasks, applications and
installations as required, according to the rules of your policy.
Empower Users and Gain Control
Allow and block the use and installation of specific binaries, packages, and bundles. By taking a simple and pragmatic approach to
allowlisting, you can gain greater control of applications in use across the business. This immediately improves security by preventing
untrusted applications from executing.
Unlock Privileged Activity
Even privileged applications and tasks that usually require admin rights are able to run under a standard user account. With Endpoint
Privilege Management for Mac, you can unlock approved system preferences such as date and time, printers, network settings, and
power management without needing admin credentials.
Take a Pragmatic Approach with Broad Rules
Broad catch-all rules provide a solid foundation, with exception handling options to handle unknown activity. Define the application and set
its identification options such as filename, hash, publisher, or URI. Then assign the application to the users who require enhanced rights
and set up any additional options, such as end user messaging and auditing.
Achieve Compliance
You will have the knowledge to discover, monitor, and manage user activity from the entire enterprise, drawing upon actionable
intelligence to make informed decisions. Graphical dashboards with real-time data will provide a broad range of reports to aid
troubleshooting and provide the information you need to proactively manage your policy on an ongoing basis.
Apply Corporate Branding
You can add your own branding to messages and prompts, with reusable messaging templates that make it easy to improve the end user
experience. You have control over text configuration.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
8
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Customizable Messaging
Working seamlessly with macOS, Endpoint Privilege Management for Mac can suppress standard, restrictive messages and allows you to
create your own customized authorization prompts to handle exceptions and enable users to request access. Set up access request
reasons, challenge / response codes, or password protection to add additional security layers, or simply improve prompts to reduce
helpdesk inquiries.
Simple, Familiar Policy Design
Firewall-style rules based on Application Groups make set up and management simple. Using the same Endpoint Privilege Management
interface and client as for Windows, you can create flexible Workstyles based on the requirements of individuals and groups of users.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
9
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Install the Endpoint Privilege Management Policy Editor
Using an administrator account, log in to the Windows computer where you want to manage Endpoint Privilege Management for Mac.
Note: Ensure you have the relevant Group Policy management tools installed on the desktop or server where you wish to
install Endpoint Privilege Management Policy Editor.
To install Endpoint Privilege Management Policy Editor, run the appropriate installation package:
l
For 32-bit (x86) systems, run PrivilegeManagementPolicyEditor_x86.exe.
l
For 64-bit (x64) systems, run PrivilegeManagementPolicyEditor_x64.exe.
Install Endpoint Privilege Management Policy Editor:
1. The installation detects if any prerequisites are needed. Click Install to install any missing prerequisites. This may take a few
minutes.
2. Once the prerequisites have been installed, the Welcome dialog box appears. Click Next to continue.
3. After reading the license agreement, select I accept the terms in the license agreement and click Next.
4. Enter your name and the name of your organization, and click Next.
5. If you want to change the default installation directory, click Change and select a different installation directory. Click Next.
6. If you are only managing Windows machines with Endpoint Privilege Management and want to evaluate it for use with McAfee
ePolicy Orchestrator, check the McAfee ePolicy Orchestrator Integration box. Otherwise, leave it unchecked and click Next.
7. Click Install to start installing Endpoint Privilege Management Policy Editor.
8. Once installed, click Finish. Endpoint Privilege Management Policy Editor has now been successfully installed.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
10
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
Install the Endpoint Privilege Management for Mac Client
Install the Endpoint Privilege Management for Mac client to apply Endpoint Privilege Management policy to macOS computers.
Endpoint Privilege Management for Mac can be installed manually. We recommend a third-party software deployment tool for larger
installations.
Note: There is no license to add during the client installation, as this is deployed with the Endpoint Privilege Management
Workstyles, so the client may be installed silently.
Requirements
For more information about the installation requirements, see Endpoint Privilege Management Release Notes
at https://www.beyondtrust.com/docs/release-notes/privilege-management/index.htm.
Install Endpoint Privilege Management for Mac
To install Endpoint Privilege Management for Mac, download and run the client installer package (*.pkg).
During the installation, the _avectodaemon account is created and added to the local Admin group. Do not remove this account from the
group.
Different Versions of Agents
In some estates, a range of different agent versions can exist together. Here are a couple of scenarios where this might occur:
l
An older version of the agent might be needed for an older OS. For example, agent version 21.7 does not support 10.14 Mojave so
an earlier version is required.
l
A company might create a pilot group to run a newer version for agent testing while the rest of the estate runs the older version.
We always retain backwards compatibility for the policies when adding new features. This allows you to configure and use new features in
your policies and use them with newer agents. On any older agents in your estate the new features will be ignored and will not affect the
function of the agents.
Configure MacOS System Settings
Endpoint Privilege Management for Mac client uses system extensions for application control where available.
Configure the following macOS system settings for Endpoint Privilege Management for Mac:
l
Authorization
l
Full Disk Access permission
You can use a macOS configuration profile (.mobileconfig file) available with the Endpoint Privilege Management for Mac download to
apply these settings. We recommend importing the configuration profile into MDM to enable the new functionality.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
11
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

To access the .mobileconfig file, you must log on to the BeyondTrust
Customer Portal and go to File Downloads. Select Endpoint Privilege
Management for Mac and the version. The File Downloads page will look
similar to the screen capture shown.
The best way to configure the system settings is using the configuration
profile provided by BeyondTrust. Optional ways are provided below.
Add Authorization
There are two ways to configure authorization on system extensions:
l
Manually: Configure Privacy & Security in System Settings.
l
MDM: Use the BeyondTrust configuration profile provided in the installer download. Alternatively, Apple provides MDM settings to
auto-authorize system extensions.
For more information, see SystemExtensions at
https://developer.apple.com/documentation/devicemanagement/systemextensions.
Grant Full Disk Access on System Extensions
The system extensions require the Full Disk Access permission. In System Settings, go to the Privacy & Security and select Full Disk
Access.
Instructions to configure disk access vary depending on the version of your OS.
For more information, see:
l
our Knowledge Base article How to Enable Full Disk Access for the Endpoint Privilege Management Components at
https://beyondtrustcorp.service-now.com/now/cwf/agent/kb_view/u_kb_template_support_how_to_
information/9fb910cb1be5bd186fe95287624bcb69
l
Change Privacy preferences on Mac at https://support.apple.com/en-ca/guide/mac-help/mh32356/12.0/mac/12.0.
Use Anti-tamper Protection
A safety mechanism in the Endpoint Privilege Management for Mac agent automatically blocks attempts to change or disable any footprint
of the agent or policies. The built-in anti-tamper protection does not require adding explicit block rules.
The anti-tamper protection prevents Standard Users from tampering with the Endpoint Privilege Management for Mac client, all platform
adapters, policies, and settings files.
By default, anti-tamper protection is turned off.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
12
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

There are two ways to turn on anti-tamper:
l
Use the Rapid Deployment Tool and distribute the settings package to endpoints
l
Use the tool installed with the Endpoint Privilege Management for Mac.
Turn on Anti-tamper Protection
From the command line, run:
sudo pmfm protection enable
Turn off Anti-tamper Protection
From the command line, run:
sudo pmfm protection disable
Confirm the Status of the Tool
sudo pmfm status
The response indicates if the tool is on or off:
{protection":{enabled":true}
Upgrade the Endpoint Privilege Management Mac Client
In an upgrade scenario, we recommend the following order of operations:
1. Update System Preferences to enable system extensions using the configuration profile (.mobileconfig file) provided by
BeyondTrust with your MDM.
2. Upgrade the Endpoint Privilege Management for Mac client.
Note: If you do not use an MDM, then update System Preferences after upgrading the client.
If you are using the install.sh or settings have been applied using the Rapid Deployment Tool, then run the installer package for the
Endpoint Privilege Management for Mac client.
The earlier version of the client is automatically uninstalled when you run the installer package.
Events are migrated as part of the upgrade.
If you are using ePO, you can manage the upgrade through ePO Server.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
13
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Uninstall Endpoint Privilege Management for Mac
Note: The uninstall scripts must be run from their default locations.
Uninstall Endpoint Privilege Management
To uninstall Endpoint Privilege Management locally on a Mac, run the following command:
sudo /usr/local/libexec/Avecto/Defendpoint/1.0/uninstall.sh
Uninstall the Mac Adapter
To uninstall the Mac adapter, run the following command. After running the uninstall script some related directories remain if they are not
empty, such as /Library/Application Support/Avecto/iC3Adapter.
sudo /usr/local/libexec/Avecto/iC3Adapter/1.0/uninstall_ic3_adapter.sh
Remove the Endpoint Privilege Management Policy
To remove the policy once you have uninstalled Endpoint Privilege Management, run the following command:
sudo rm -rf /etc/defendpoint
Note: Do not remove the Endpoint Privilege Management policy unless you have already uninstalled Endpoint Privilege
Management.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
14
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Launch the Endpoint Privilege Management Policy Editor
The Endpoint Privilege Management Policy Editor is accessed as a snap-in to the Microsoft Management Console (MMC.exe).
From your administrator account, run MMC.exe. Type MMC into the Search Box from the Start Menu and press the Enter key.
We will now add Endpoint Privilege Management for Mac as a snap-in to the console.
1. Select File from the menu bar and select Add/Remove Snap-in.
2. Scroll down the list and select the Endpoint Privilege Management Settings snap-in. Click Add and then click OK.
3. Optionally, select File > Save as and save a shortcut for the snap-in to the desktop as Endpoint Privilege Management.
4. Select the Endpoint Privilege Management Settings node in the left-hand pane and select the operating system node to display
the main screen in the details pane.
Navigate the Endpoint Privilege Management Policy Editor
The left-hand pane containing the Endpoint Privilege Management
Settings item is referred to as the tree pane. The folders beneath Endpoint
Privilege Management Settings in the tree pane are referred to as nodes.
The middle pane, which displays content relevant to the selected node, is
referred to as the details pane.
If you expand the Endpoint Privilege Management Settings node, you will see three nodes:
l
Windows: Create Endpoint Privilege Management for Windows endpoints.
l
OS X: Create Endpoint Privilege Management for MacOS endpoints.
l
Licensing: Manage Endpoint Privilege Management licenses.
If you expand the OS X node you will see three nodes:
l
Workstyles: Assign privileges to applications.
l
Application Groups: Define logical groupings of applications.
l
Messages: Define end user messages.
Once a Workstyle has been created and selected in the tree pane, the Workstyle tabs will be displayed in the details pane.
Automatic Save
By default, the Endpoint Privilege Management Settings editor will automatically save any changes back to the appropriate GPO or local
XML file if you are using the standalone console.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
15
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Automatic saving can be disabled, by deselecting the Auto Commit Settings menu option on the Endpoint Privilege Management
Settings node, but is not recommended unless you have performance issues. If you deselect the Auto Commit Settings option, then
you must select the Commit Settings menu option to manually save any changes back to the GPO. The Auto Commit Settings option is
persisted to your user profile, so it will be set for all future editing of Endpoint Privilege Managementfor Mac settings.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
16
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Policies and Templates
A policy is made up of one or more items from the following groups:
l
Workstyles: A Workstyle is part of a policy. It's used to assign Application Rules for users. You can create Workstyles by using the
WorkStyle Wizard or by importing them.
l
Application Groups: Application Groups are used by Workstyles to group applications together to apply certain Endpoint
Privilege Management for Mac behavior.
l
Messages: Messages are used by Workstyles to provide information to the end user when Endpoint Privilege Management for
Mac has applied certain behavior you have defined and needs to notify the end user.
Users
Disconnected users are fully supported by Endpoint Privilege Management for Mac. When receiving policies from Trellix ePO, EPM-M
automatically caches all the information required to work offline, so the settings will still be applied if the client is not connected to the
corporate network. Any changes made to the policy will not propagate to the disconnected computer until the McAfee Agent reestablishes
a connection to the ePO Server.
Policies
Policies are applied to one or more endpoints. The Policy Summary screen summaries for the number of Workstyles, Application
Groups, and Messages in the policy. As this is a blank policy, all summaries will be zero.
Each item summary includes an Edit <Item> button, which allows you to jump to that section of the policy.
EPM-M incorporates an autosave, autosave recovery, and concurrent edit awareness feature to reduce the risk or impact of data loss and
prevent multiple users from overwriting individual polices.
A template is a configuration that is merged with your existing policy. A template also consists of any number of Workstyles, Application
Groups, Content Groups, Messages, and Custom Tokens.
Edit Group Policy
To edit policy, we recommend you use the Privilege Management Console.
For more information, see EPM Administration Guide at https://www.beyondtrust.com/docs/privilege-
management/console/pm-cloud/index.htm.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
17
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Privilege Management Settings
You can right-click the Privilege Management Settings node to access the following commands.
You can click Tools in the right-hand panel to access the Response Code Generator.
By default, Auto Commit Settings is selected. This means any changes made here are saved and applied using Group Policy.
Alternatively, you can clear Auto Commit Settings and select Commit Settings when you specifically want those settings to apply.
For more information, see "Endpoint Privilege Management for Mac Response Code Generator" on page 21.
The following options are also available:
Create
Creates a policy. This will delete any existing policy for all operating systems. If you have an existing policy, you are prompted to remove
all existing settings when you click Create. Click Yes to delete your existing policy and create a new one or No to keep your existing policy.
Delete
Deletes your existing policy. You are prompted to remove all existing settings when you click Delete. Click Yes to delete your existing
policy or No to keep your existing policy.
Delete Items and Conflict Resolution
Some items within Privilege Management Settings are referenced in other areas, such as Application Groups and Messages. These
items can be deleted at any time, and if they are not referenced elsewhere, they delete without any further action required.
When an item is deleted, the Policy Editor checks for any conflicts which may need to be resolved. If the item you attempt to delete is
already in use elsewhere in your settings, then a conflict will be reported and must be resolved.
You can review each detected conflict and observe the automatic resolution which will take place if you proceed. If more than one conflict
is reported, use the Next conflict and Previous conflict links to move between conflicts.
If you want to proceed, click Resolve All to remove the item from the areas of your Privilege Management Settings where it is currently
in use.
Export
Policies can be imported to and exported from Group Policy as .XML files, in a format common to other editions of Endpoint Privilege
Management, such as the Endpoint Privilege Management ePO Extension. This allows for policies to be migrated and shared between
different deployment mechanisms.
To export a policy, click Export and give the file a name. Click Save.
Import
Policies can be imported to and exported from Group Policy as .XML files, in a format common to other editions of Endpoint Privilege
Management, such as the Endpoint Privilege Management ePO Extension. This allows for policies to be migrated and shared between
different deployment mechanisms.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
18
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

To import a policy, click Import, navigate to the policy XML, and click Open.
Import Template
Allows you to import template policies.
For more information, see "Templates" on page 22.
Save Report
You can obtain a report of your policy which can be saved locally, if required.
Set Challenge/Response Shared Key
This allows you to set the Challenge/Response Shared Key for the policy. This is encrypted once you have set it. This key is then required
by the challenge/response generator to generate response codes. The only way to change the Challenge/Response Shared Key is by
setting a new one.
Show Hidden Groups
You can show or hide Application Groups.
To show groups that have been hidden by default, right-click on the Privilege Management Settings node and select Show Hidden
Groups. You can hide the groups again by clearing Show Hidden Groups.
View
This allows you to view the Workstyles Editor (default).
You can review each detected conflict and observe the automatic resolution which will take place if you proceed. If more than one conflict
is reported, use the Next conflict and Previous conflict links to move between conflicts.
If you want to proceed, click Resolve All to remove the item from the areas of your Privilege Management Settings where it is currently
in use.
License
Endpoint Privilege Management for Mac requires a valid license code to be entered in the Policy Editor. If multiple policies are applied to
an endpoint, you need at least one valid license code for one of those policies.
For example, you could add the license to a policy that is applied to all managed endpoints, even if it doesn't have any Workstyles. This
ensures all endpoints receive a valid license if they have Endpoint Privilege Management for Mac installed. If you are unsure, then we
recommend you add a valid license when you create the policy.
Insert a License
1. Click No License. Click to enter a license code to enter a license if one doesn't already exist, or Valid License if you want to
enter an additional license code.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
19
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

2. Paste your Endpoint Privilege Management for Mac license code and click Add. The license details are shown.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
20
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Endpoint Privilege Management for Mac Response Code Generator
The Response Code Generator allows you to generate a response code using the PGChallengeResponseUI utility.
To generate a Response Code from Endpoint Privilege Management Settings:
1. Click the Tools link from the right-hand panel of Endpoint Privilege Management Settings.
2. Click Launch Response Code Generator.
3. Enter your shared key and the challenge code. The response code
is shown in the third text field.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
21
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Templates
Templates can be imported into your Endpoint Privilege Management for Mac settings. You can choose to merge them into your existing
policy; otherwise, the template overwrites your existing policy.
Note: Be careful when merging policies with production policies. If No is selected, then the existing policy settings and license
information are removed. If Yes is selected, then the template is added to the existing policy.
macOS QuickStart
The QuickStart for macOS policy contains Workstyles, Application Groups, and Messages configured with Endpoint Privilege
Management for Mac and Application Control. The QuickStart policy has been designed from BeyondTrust’s experiences of implementing
the solution across thousands of customers, and is intended to balance security with user freedom. As every environment is different, we
recommend you thoroughly test this configuration to ensure it complies with the requirements of your organization.
This template policy contains the following elements:
Workstyles
l
All Users
l
High Flexibility
l
Medium Flexibility
l
Low Flexibility
Application Groups
l
(Default) Any Application
l
(Default) Any Authorization Prompt
l
(Default) Any Signed Authorization Prompt
l
(Default) Any Sudo Command
l
(Default) Any Trusted & Signed Authorization Prompt
l
(Default) Authorize - Delete from /Applications
l
(Default) Authorize - Install to /Applications
l
(Default) Authorize - System Trusted
l
(Default) Passive - System Trusted
l
(Default) Endpoint Privilege Management Tools
l
(Recommended) Restricted Functions
l
Authorize - All Users (Business Apps)
l
Authorize - All Users (macOS Functions)
l
Authorize - High Flexibility
l
Authorize - Medium Flexibility
l
Authorize - Low Flexibility
l
Block - Blocked Apps
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
22
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Passive - Allowed Function & Apps
l
Passive - High Flexibility (Business Apps)
l
Passive - Low Flexibility (Business Apps)
l
Passive - Medium Flexibility (Business Apps)
Messages
l
Allow Message (Authentication & Reason)
l
Allow Message (Support Desk)
l
Allow Message (Yes / No)
l
Allow Message (select Reason)
l
Block Message
QuickStart Policy Summary
By using and building on the QuickStart policy, you can quickly improve your organization's security without having to monitor and analyze
your users' behavior first and then design and create your Endpoint Privilege Management for Mac configuration.
After the QuickStart policy has been deployed to groups within your organization, you can start to gather information on your users'
behavior. This will provide you with a better understanding of the applications being used within your organization, and whether they
require admin rights, need to be blocked, or need authorization for specific users.
This data can then be used to further refine the QuickStart policy to provide more a tailored Endpoint Privilege Management for Mac
solution for your organization.
macOS Workstyles
The QuickStart policy contains four Workstyles that should be used together to manage all users in your organization.
All Users
This Workstyle contains a set of default rules that apply to all standard users regardless of what level of flexibility they need.
The All Users Workstyle contains rules to:
l
Block any applications that are in the Block Applications group.
l
Allow BeyondTrust Support tools.
l
Allow approved standard user applications to run passively.
l
Allow and authorize the install and delete of bundles to the /Applications/ directory.
High Flexibility
This Workstyle is designed for users that require a lot of flexibility such as developers.
The High Flexibility Workstyle contains rules to:
l
Allow known allowed business applications and operating system functions to run.
l
Allow users to run signed applications with admin rights.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
23
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Allow users to run unknown applications with admin rights once they have confirmed the application should be elevated.
l
Allow unknown business application and operating system functions to run on-demand.
Medium Flexibility
This Workstyle is designed for users that require some flexibility such as sales engineers.
The Medium Flexibility Workstyle contains rules to:
l
Allow known allowed business applications and operating system functions to run.
l
Allow users to run signed applications with admin rights once they have confirmed the application should be elevated.
l
Prompt users to provide a reason before they can run unknown applications with admin rights.
l
Allow unknown business application and operating system functions to run on-demand.
l
Restricted OS functions that require admin rights are prevented and require support interaction.
Low Flexibility
This Workstyle is designed for users that don't require much flexibility such as helpdesk operators.
The Low Flexibility Workstyle contains rules to:
l
Prompt users to contact support if a trusted or untrusted application requests admin rights.
l
Prompt users to contact support if an unknown application tries to run with support authorization.
l
Allow known approved business applications and operating system functions to run.
macOS Workstyle Parameters
You can customize text and strings used for end user messaging and auditing.
Parameters are identified as any string surrounded by brackets ([ ]), and if detected, the Endpoint Privilege Management client attempts to
expand the parameter. If successful, the parameter is replaced with the expanded property. If unsuccessful, the parameter remains part of
the string. The table below shows a summary of available parameters.
Parameter Description
[PG_APP_DEF] The name of the Application Rule that matched the application
[PG_APP_GROUP] The name of the Application Group that contained a matching Application Rule
[PG_COMPUTER_NAME] The NetBIOS name of the host computer
[PG_PROG_CMD_LINE] The command line of the application being run
[PG_PROG_NAME] The program name of the application
[PG_PROG_PATH] The full path of the application file
[PG_PROG_PROD_VERSION] The product version of the application being run
[PG_PROG_PUBLISHER] The publisher of the application
[PG_PROG_TYPE] The type of application being run
[PG_WORKSTYLE_NAME] The name of the Workstyle
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
24
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

macOS Application Groups
l
(Default) Any Application: Contains all application types and is used as a catch-all for unknown applications.
l
(Default) General - Any Authorization Prompt: This group contains application types that request admin rights regardless of
trust or code signature.
l
(Default) General - Any Signed Authorization Prompt: This group contains application types that request admin rights and
meet macOS code signature requirements
l
(Default) General - Any Trusted & Signed Authorization Prompt: This group contains macOS built-in applications that request
admin rights and meet macOS code signature requirements
l
(Default) Passive - System Trusted: This group contains system applications that are allowed for all users.
l
(Default) Authorize - System Trusted: This group contains system applications requiring authorization that are allowed for all
users.
l
(Default) Any Sudo Commands: Contains all sudo commands and is used as a catch-all for unknown sudo commands.
l
(Default) Privilege Management Tools: Contains BeyondTrust binaries and application bundles used to gather logging or
otherwise modify Endpoint Privilege Management for Mac settings.
l
(Default) Authorize - System Trusted: Contains operating system functions that are authorized for all users.
l
(Recommended) Restricted Functions: This group contains OS functions that are used for system administration and trigger an
authorization prompt when they are executed.
l
Authorize – All Users (Business Apps): Contains applications such as line-of-business applications that are authorized for all
users, regardless of their flexibility level.
l
Authorize – All Users (macOS Functions): This group is designed to contain system preferences and other built-in macOS
functions that trigger an authorization prompt when they are executed, regardless of the user’s flexibility level.
l
Authorize - High Flexibility: Contains the applications that require authorization that should only be provided to high flexibility
users.
l
Authorize - Low Flexibility: Contains the applications that require authorization that should only be provided to low flexibility
users.
l
Authorize - Medium Flexibility: Contains the applications that require authorization that should only be provided to medium
flexibility users.
l
Block – Blocked Apps: This group contains applications that are blocked for all users.
l
Passive – Allowed Functions & Apps: This group contains applications that are allowed for all users.
l
Passive – High Flexibility (Business Apps): This group contains applications that are allowed for High Flexibility users without
providing admin authorization.
l
Passive – Low Flexibility (Business Apps): This group contains applications that are allowed for Low Flexibility users without
providing admin authorization.
l
Passive – Medium Flexibility (Business Apps): This group contains applications that are allowed for Medium Flexibility users
without providing admin authorization.
macOS Messages
The following messages are created as part of the QuickStart policy and are used by some of the Application Rules:
l
Allow Authorize (Authentication & Reason): Asks the user to enter their password and provide a reason before the application
is authorized to run.
l
Allow Message (Yes / No): Asks the user to confirm that they want to proceed to authorize an application to run.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
25
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Allow Message (Select Reason): Asks the user to select a reason from a drop-down list before the application is authorized to
run.
l
Allow Message (Support Desk): Presents the user with a challenge code and asks them to obtain authorization from the support
desk. Support can either provide a response code or a designated, authorized user can enter their login details to approve the
request.
l
Block Message: Warns the user that an application has been blocked.
Customize the QuickStart Policy
Before deploying the QuickStart policy to your users, you need to make some company-specific customizations to the standard template.
At a minimum you need to:
l
Configure the users or groups that can authorize requests that trigger messages.
l
Customize the messaging with you company logo and wording
l
Assign users and groups to the high, medium, and low flexibility Workstyles.
l
Populate the Block Applications Application Group with any applications you want to block for all users.
l
Set your shared key so you can generate an Endpoint Privilege Management for Mac Response code.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
26
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Mac Specific
Multiple Mac Policies
For Mac estates being managed by ePO, multiple policies being applied simultaneously is supported, for example:
l
epo.xml
l
epo001.xml
l
epo002.xml
In the example above, if the policy precedence is set for ePO policies, then rules processing will first check the rules in epo.xml. If no rules
are found for the process in this policy, then it will go through the epo001.xml. Each policy is processed in an alpha-numeric/C locale
order. This continues until the process hits a rule or the dppolicyserverd reads all of the policies without finding a match.
If multiple policies are loaded, only one of them requires an Endpoint Privilege Management for Mac license. We recommend you do not
use multiple licenses in this configuration. Each policy can have a different Challenge-Response key.
Copy and pasted policies with altered rules are still processed, the dppolicyserverd log outputs whether it replaced GUIDs when loading
them into memory if it was a duplicate.
Mac Application Templates
Endpoint Privilege Management for Mac ships with some standard application templates to simplify the definition of applications that are
part of the operating system. The standard application templates are split into categories:
l
System Preference Panes
l
Bundles
l
Binaries
Each category then has a list of applications for that category. Picking an application will cause the application to be prepopulated with the
appropriate information.
Add Endpoint Privilege Management for Mac Settings to a Mac Client Computer
Endpoint Privilege Management for Mac settings are stored in the file /etc/defendpoint/local.xml, and can be overwritten with an
exported XML file from the MMC. To prevent any invalid permissions being applied, we recommend this file be replaced using the
following command. In this example, the source XML file is located on your Desktop:
sudo cp ~/Desktop/local.xml /etc/defendpoint/local.xml
Endpoint Privilege Management for Mac will apply the new settings immediately, and does not require a restart.
Note: If all policies are deleted, the local.xml policy is regenerated. The regenerated local.xml policy will not contain any
license or rules.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
27
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Mac Sudo Command Arguments Not Supported
The following arguments are not supported by Endpoint Privilege Management for Mac when you're using sudo:
Option (single dash) Option (double dash) Description
-A --askpass use a helper program for password prompting
-C num --close-from=num close all file descriptors >= num
-E --preserve-env preserve user environment when running command
-g group --group=group run command as the specified group name or ID
-H --set-home set HOME variable to target user's home dir
-h host --host=host run command on host (if supported by plugin)
-K --remove-timestamp remove timestamp file completely
-k --reset-timestamp invalidate timestamp file
-l --list list user's privileges or check a specific command; use twice for longer format
-n --non-interactive non-interactive mode, no prompts are used
-P --preserve-groups preserve group vector instead of setting to target's
-p prompt --prompt=prompt use the specified password prompt
-U user --other-user=user in list mode, display privileges for user
-u user --user=user run command (or edit file) as specified user name or ID
-v --validate update user's timestamp without running a command
Use Centrify
If you are using Centrify to bind macOS endpoints to Active Directory, contact BeyondTrust Technical Support for assistance.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
28
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Third Party Licensing Information
We use the following third party software:
l
Sudo
l
SwiftyJSON
l
Google Protobuf
Sudo Copyright Notice
Sudo is distributed under the following license:
Copyright (c) 1994-1996, 1998-2019
Todd C. Miller <[email protected]>
Permission to use, copy, modify, and distribute this software for any purpose with or without fee is hereby granted, provided that the above
copyright notice and this permission notice appear in all copies.
THE SOFTWARE IS PROVIDED "AS IS" AND THE AUTHOR DISCLAIMS ALL WARRANTIES WITH REGARD TO THIS SOFTWARE
INCLUDING ALL IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS. IN NO EVENT SHALL THE AUTHOR BE LIABLE
FOR ANY SPECIAL, DIRECT, INDIRECT, OR CONSEQUENTIAL DAMAGES OR ANY DAMAGES WHATSOEVER RESULTING FROM
LOSS OF USE, DATA OR PROFITS, WHETHER IN AN ACTION OF CONTRACT, NEGLIGENCE OR OTHER TORTIOUS ACTION,
ARISING OUT OF OR IN CONNECTION WITH THE USE OR PERFORMANCE OF THIS SOFTWARE.
Sponsored in part by the Defense Advanced Research Projects Agency (DARPA) and Air Force Research Laboratory, Air Force Materiel
Command, USAF, under agreement number F39502-99-1-0512.
SwiftyJSON Copyright Notice
The MIT License (MIT)
Copyright (c) 2017 Ruoyu Fu
Permission is hereby granted, free of charge, to any person obtaining a copy of this software and associated documentation files (the
"Software"), to deal in the Software without restriction, including without limitation the rights to use, copy, modify, merge, publish,
distribute, sublicense, and/or sell copies of the Software, and to permit persons to whom the Software is furnished to do so, subject to the
following conditions:
The above copyright notice and this permission notice shall be included in all copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT
LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN
NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY,
WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE
SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
Google Protobuf Copyright Notice
Copyright 2008 Google Inc. All rights reserved.
Redistribution and use in source and binary forms, with or without modification, are permitted provided that the following conditions are
met:
* Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
29
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

* Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the
documentation and/or other materials provided with the distribution.
* Neither the name of Google Inc. nor the names of its contributors may be used to endorse or promote products derived from this software
without specific prior written permission.
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS" AND ANY EXPRESS OR IMPLIED
WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A
PARTICULAR PURPOSE ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE LIABLE
FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR
TORT (INCLUDING NEGLIGENCE OR OTHERWISE) ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF
ADVISED OF THE POSSIBILITY OF SUCH DAMAGE.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
30
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Configure Caching on Policies
Cache policy rules to enhance rule processing and reduce the possibility of performance issues. Endpoint Privilege Management for Mac
caching detects and stores user actions that have been repeated recently. This improves performance during user actions which require
many execution events within a short period of time (for example, compiling software).
Starting in version 24.1, caching is turned on by default.
Overview
Events that are cached include allowed binary execution events with no user interaction involved.
To protect your data, events that might be vulnerable to attack are not cached, and include:
l
Unsigned binaries or sudo commands.
l
Self-signed binaries.
l
If the binary is contained in a rule which also matches on arguments.
Specifications
l
The cache is stored in the memory of the endpoint security framework.
l
The maximum size of the cache is 1 Megabyte.
l
Currently stores up to approximately 130,000 entries.
l
Every entry has a 30 seconds expiry time interval.
Configure Caching
Caching is packaged as part of the pmfm tool installed with Endpoint Privilege Management for Mac.
To turn on caching, run the following command:
sudo pmfm caching enable
To turn off caching, run the following command:
sudo pmfm caching disable
Change the User Interface
Starting in version 24.1, a new Apple-compatible UI is available. You can, however, revert to the previous UI.
The default state shows the new UI. Use the pmfm tool to change to the legacy UI.
Turn on Legacy UI
From the command line, run:
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
31
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

sudo pmfm legacyUI enable
Turn off Legacy UI
From the command line, run:
sudo pmfm legacyUI disable
To confirm the status of the LegacyUI setting, run:
sudo pmfm status
The response indicates if the tool is on or off:
{LegacyUI":{enabled":true}}
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
32
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Policies
A policy is built with the following optional components:
l
Workstyles: A Workstyle is part of a policy. It's used to assign Application Rules for users. You can create Workstyles using the
WorkStyle Wizard or by importing them.
l
Application Groups: Application Groups are used by Workstyles to group applications together to apply certain Endpoint
Privilege Management for Mac behavior.
l
Messages: Messages are used by Workstyles to provide information to the end user when Endpoint Privilege Management for
Mac has applied certain behavior you have defined and needs to notify the end user.
Note: Using .MPKG (multiple package) format or launching multiple .PKG files at once is not supported and is blocked by
Endpoint Privilege Management for Mac.
Note: Mac Policies are not applied to the root user.
For more information, see the following sections:
l
"Workstyles" on page 34
l
"Application Groups" on page 41
l
"Messages" on page 67
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
33
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Workstyles
Workstyles are used to assign Application Groups for a specific user or group of users. The Workstyle Wizard can generate Application
Rules depending on the type of Workstyle you choose.
For more information, see the following sections:
l
"Application Groups" on page 41
l
"Create Workstyles" on page 36
Workstyle Wizard
The Workstyle Wizard guides you through the process of creating a Workstyle. The options you select determine the function of the
Workstyle.
1. Navigate to the OS X > Workstyles node.
2. Right-click the Workstyles node, and then click Create Workstyle on the top-right. The Workstyle Wizard is displayed.
3. You can optionally enter a license code at this stage or you can enter it later once the Workstyle has been created.
4. You can choose from Controlling or Blank for your Workstyle. A controlling Workstyle allows you to apply rules for access to
privileges and applications. A blank Workstyle allows you to create an empty Workstyle without any predefined elements. If you
selected a blank Workstyle, the next screen is Finish as there is nothing to configure.
5. Filtering (Controlling Workstyle only). This determines who will receive this Workstyle. You can choose from Standard users only
or everyone. If you apply it to everyone, it will apply to Administrators. You can modify the filters and apply more detailed filtering
once the Workstyle has been created.
6. Capabilities (Controlling Workstyle only). Allows you to choose Endpoint Privilege Management, Application Control, or both. If
you don't select either capabilities, the next screen is Finish. This Workstyle would only contain filtering information.
7. Endpoint Privilege Management (Controlling Workstyle with the Endpoint Privilege Management capability). Allows you to
choose how you manage Authorization prompts including sudo control and Installer privileges.
Note: If you select Present users with a challenge code from the dropdown, you are prompted to configure the challenge
and response functionality at the end of creating your Workstyle, if your policy doesn't already have one.
8. Application Control (Controlling Workstyle with the Application Control capability). Allows you to choose:
l
How you want to apply application control. You can choose from an allowlist or blocklist approach. We recommend you use
an allowlist approach.
o
As an allowlist: How you want to handle non-allowed applications.
o
As a blocklist: How you want to handle blocked applications.
9. Finish. Allows you to enter a Name and Description for your new policy. If the Workstyle has been configured to use a Challenge
/ Response message and the policy doesn't have an existing key, you will be asked to set a key. You can check the box on this
screen to activate this Workstyle immediately or you can clear the box to continue configuring the Workstyle before you apply it to
your endpoints.
Depending on the type of Workstyle you created and any capabilities that have been included, Endpoint Privilege Management for Mac
will auto-generate certain Application Groups (containing rules) and Messages. Filters are applied and subsequently configured as part of
the Workstyle.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
34
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

For more information, see the following sections:
l
"Challenge / Response Authorization" on page 83
l
"Application Groups" on page 41
l
"Messages" on page 67
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
35
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Create Workstyles
The Workstyle Wizard guides you through the process of creating an Workstyle. The options you select determine the function of the
Workstyle.
1. Navigate to the OS X > Workstyles node.
2. Right-click the Workstyles node, and then click Create Workstyle on the top-right. The Workstyle Wizard is displayed.
3. You can optionally enter a license code at this stage or you can enter it later once the Workstyle has been created.
4. You can choose from Controlling or Blank for your Workstyle. A controlling Workstyle allows you to apply rules for access to
privileges and applications. A blank Workstyle allows you to create an empty Workstyle without any predefined elements. If you
select a blank Workstyle, the next screen is Finish as there is nothing to configure.
5. Filtering (Controlling Workstyle only). This determines who will receive this Workstyle. You can choose from Standard users only
or everyone. If you apply it to everyone, it will apply to Administrators. You can modify the filters and apply more detailed filtering
once the Workstyle has been created.
6. Capabilities (Controlling Workstyle only). Allows you to choose Endpoint Privilege Management, Application Control, or both. If
you don't select either capabilities, the next screen is Finish. This Workstyle would only contain filtering information.
7. Privilege Management (Controlling Workstyle with the Endpoint Privilege Management capability). Allows you to choose how
you manage Authorization prompts including sudo control and Installer privileges.
Note: If you select Present users with a challenge code from the dropdown, you are prompted to configure the challenge
and response functionality at the end of creating your Workstyle, if your policy doesn't already have one.
8. Application Control (Controlling Workstyle with the Application Control capability). Allows you to choose:
l
How you want to apply application control. You can choose from an allowlist or blocklist approach. We recommend you use
an allowlist approach.
o
As an allowlist: How you want to handle non-allowed applications.
o
As a blocklist: How you want to handle blocked applications.
9. Finish. Allows you to enter a Name and Description for your new policy. If the Workstyle has been configured to use a Challenge
/ Response message and the policy doesn't have an existing key, you will be asked to set a key. You can check the box on this
screen to activate this Workstyle immediately or you can clear the box to continue configuring the Workstyle before you apply it to
your endpoints.
Depending on the type of Workstyle you create and any capabilities that have been included, Endpoint Privilege Management for Mac will
auto-generate certain Application Groups (containing rules) and Messages. Filters are applied and subsequently configured as part of the
Workstyle.
For more information, see the following sections:
l
"Challenge / Response Authorization" on page 83
l
"Application Groups" on page 41
l
"Messages" on page 67
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
36
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Disable or Enable Workstyles
By default, a Workstyle is disabled when initially created. Enable a Workstyle when configuration is complete and ready for the production
environment.
Disable the Workstyle whenever you need to change the configuration.
To enable or disable a Workstyle:
1. Navigate to the policy and select the Workstyles node. You can
see which policies are disabled and enabled in the list.
2. Right-click on the Workstyle and click Disable Workstyle to disable
it or Enable Workstyle to enable it.
In the above example, the General Rules Workstyle is enabled and the High Flexibility Workstyle is disabled.
Workstyle Precedence
If you have multiple Workstyles, they are evaluated in the order they are listed. Workstyles that are higher in the list have a higher
precedence. Once an application matches a Workstyle, no further Workstyles are processed for that application, so it is important you
order your Workstyles correctly, because an application could match more than one Workstyle.
To change the precedence of a Workstyle:
1. Select the Workstyles node in the left pane.
2. Right-click and choose from the options:
l
Move Top
l
Move Up
l
Move Down
l
Move Bottom
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
37
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Workstyle Summary
You can view a summary of the Workstyles, Application Groups, and Messages in your policy for Mac by clicking the OS X node in the
policy editor.
Some of these tabs may not be displayed if they have not been configured in your policy.
Overview
The Overview tab allows you to quickly access the following features of your policy:
l
General: Allows you to edit the description of your Workstyle and enable or disable it.
l
Totals: Allows you to configure Application Rules.
l
Filters: Allows you to configure filters.
Application Rules
Application Rules are applied to Application Groups. Application Rules can be used to enforce allowlisting, monitoring, and assigning
privileges to groups of applications. They are a set of rules that apply to the applications listed in the Application Group.
You need an Application Group before you can create an Application Rule.
Application Rules are color coded in the interface:
l
Green: The default action is Passive (No Change) or Allow.
l
Orange: The default action is Block.
For more information, see "Application Groups" on page 41.
Insert an Application Rule
Click Application Rules to view, create, or modify the following for each Application Rule:
Option Description
Target Application Group Select from the Application Groups list.
Default Action Select from Passive (No Change), Allow Execution, or Block
Execution. This is what will happen if the application in the targeted
Application Group is launched by the end user.
Default End User Message Select if a message will be displayed to the user when they launch the
application. We recommend using Messages if you're blocking the
execution of the application so the end user has some feedback on why the
application doesn't launch.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
38
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Option Description
Auditing
Raise an Event Whether or not you want an event to be raised if this Application Rule is
triggered. This will forward to the local event log file.
BeyondInsight Reporting Options
BeyondInsight Events When configured, sends BeyondInsight events to BeyondInsight.
Endpoint Privilege Management Reporting When configured, sends Endpoint Privilege Management Reporting events
to BeyondInsight.
For more information, see "Application Groups" on page 41.
Application Rule Precedence
If you add more than one Application Rule to a Workstyle, then entries that are higher in the list will have a higher precedence. Once an
application matches an Application Rule, no further rules or Workstyles will be processed. If an application could match more than one
Workstyle or rule, then it is important you order both your Workstyles and rules correctly. You can move Application Rules up and down to
change the precedence.
Filters
The Filters tab of a Workstyle can be used to further refine when a Workstyle will be applied. By default, a Workstyle will apply to all users
and computers who receive it. However, you can add one or more filters that will restrict the application of the Workstyle:
Account Filters
Account filters specify the users and groups the Workstyle will be applied to.
Note: When a new Workstyle is created, a default account filter will be added to target either Standard users only or
Everyone (including administrators), depending on your selection in the Workstyle Wizard.
To restrict a Workstyle to specific groups or users, you can filter on the Account Name, UID/GID, or both.
1. Expand the appropriate Workstyle in the left pane and click Filters.
2. Select Add a new local OS X account or Add a new domain account if you want to use Windows AD to create your filters. If
you choose this option, you need to create a mapping between your Windows SID macOS UID/GUID. You can choose to filter by
User or Group.
l
For User, you can match on the Account Name, the User ID, or both. In the instance of both, they both must match for the
filter to be applied. The Account Name is not case sensitive.
l
For Group you can match on the Group Name, the Group ID, or both. In the instance of both, they both must match for
the filter to be applied. The Group Name is not case sensitive.
3. Click OK to finish configuring your filter.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
39
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

By default, an account filter will apply if any of the user or group accounts in the list match the user. If you have specified multiple user and
group accounts within one account filter, and want to apply the Workstyle only if all entries in the account filter match, then check the box
at the top of the screen that says All items below should match.
You can add more than one account filter if you want the user to be a member of more than one group of accounts for the Workstyle to be
applied.
If an account filter is added, but no user or group accounts are specified, a warning will be displayed advising No accounts added, and the
account filter will be ignored.
Note: If All items below should match is selected, and you have more than one user account listed, the Workstyle will never
apply, as the user cannot match two different user accounts.
For more information, see Clarification regarding the status of Identity Management for Unix (IDMU) & NIS Server Role in
Windows Server 2016 Technical Preview and beyond at https://docs.microsoft.com/en-
us/archive/blogs/activedirectoryua/identity-management-for-unix-idmu-is-deprecated-in-windows-server.
Computer Filters
A computer filter can be used to target specific computers. You can specify a computer using either its host name, or by an IP address.
To restrict the Workstyle to specific computers by IP address:
1. Select the Filters tab, and then click Add a new filter.
2. Click Add a Computer Filter > Add a new IP rule. The Add IP rule dialog box appears.
3. Enter the IP address manually, in the format 123.123.123.123.
4. Click Add.
Note: You can also use the asterisk wildcard (*) in any octet to include all addresses in that octet range, for example,
192.168.*.*. Alternatively, you can specify a particular range for any octet, for example, 192.168.0.0-254. Wildcards and
ranges can be used in the same IP Address, but not in the same octet.
To restrict the Workstyle to specific computers by hostname:
1. Select the Filters tab, and then click Add a Filter.
2. Click Add a Computer Filter > Add a new hostname rule. The Add hostname rule dialog box appears.
3. Enter a hostname, or alternatively browse for a computer. You can use the * and ? wildcard characters in hostnames.
4. Click Add.
Note: By default, a computer filter is applied if any of the computers or IP Addresses in the list match the computer or client. If
you specified multiple entries, and want to apply the Workstyle only if all entries in the computer filter match, then check the
option All items below should match.
If a computer filter is added, but no host names or IP addresses are specified, a warning is displayed advising No rules added, and the
computer filter is ignored.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
40
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Application Groups
Application Groups are used to define logical groupings of applications.
Application Groups are assigned to Workstyles, so you must define Application Groups for all of the applications you want to assign to a
Workstyle.
Create Application Groups
To create an Application Group:
1. Navigate to the OS X > Application Groups node.
2. Right-click the Application Groups node, and then click New Application Groups on the top-right. The Workstyle Wizard is
displayed.
3. Enter a name and a description (if required) for the new Application Group. Click OK to save your new Application Group.
View or Edit the Properties of an Application Group
Each Application Group has a name, an optional description, and can be hidden from the policy navigation tree. You can edit these in the
properties for the Application Group.
To view the properties of an Application Group:
1. Navigate to the OS X > Application Groups node.
2. Right-click the Application Groups and click Properties to view the properties. Make any changes you require and click OK to
save the new properties.
Delete an Application Group
Application Groups are usually mapped to one or more Application Rule in a Workstyle. If you attempt to delete an Application Rule that is
mapped to an Application Group, you are notified of this before you continue. If you continue to delete the Application Group, the
associated Application Rule in the Workstyle is also deleted.
To delete an Application Group:
1. Navigate to the OS X > Application Groups node.
2. Right-click on the Application Group you want to delete and click Delete.
3. If there aren't any Application Rules in the Workstyle using that Application Group, then it is deleted. If there are Application Rules
in the Workstyle referencing that Application Group, then you are prompted to check the reference before you continue. If you click
OK, then both the Application Group and the Application Rule referencing it are deleted from your policy. If you don't want to do
this, click Cancel.
Duplicate an Application Group
You can duplicate an Application Group if you need a new Application Group containing the same applications as an existing Application
Group. You can edit a duplicated Application Group independently of the Application Group it was duplicated from.
To duplicate an Application Group:
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
41
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

1. Navigate to the OS X > Application Groups node.
2. Right-click on the Application Group you want to duplicate and click Copy.
3. Select the Application Groups node, right-click, and select Paste. This will make a new copy of the Application Group and all the
Application Rules it contained.
4. A new duplicate Application Group with an incremental number in brackets appended to the name will be created that you can
add applications to.
Rule Precedence
If you add more than one Application Rule or content rule to a Workstyle, then entries higher in the list will have a higher precedence. Once
a target matches a rule, no further rules or Workstyles will be processed for that target. If a target could match more than one Workstyle or
rule, then it is important you order both your Workstyles and rules correctly.
To change the precedence of a rule within a Workstyle:
1. Expand the relevant Workstyle and then select the rule type tab: Application, On-Demand, or Content.
2. Right click on the rule and use the following options to change the rule precedence:
l
Move Top
l
Move Up
l
Move Down
l
Move Bottom
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
42
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Application Definitions
Note: All matching criteria are case sensitive on macOS.
Application definitions allow you to target applications based on specific properties. When an application is executed, Endpoint Privilege
Management for Mac will query the properties of the application and attempt to match them against the matching criteria in the definition. If
a match is made, then the rule is applied. If any of the matching criteria do not match, then neither will the definition, and Endpoint Privilege
Management for Mac will attempt to match against subsequent definitions in the Application Group.
Endpoint Privilege Management for Mac will continue this process for subsequent Application Groups defined in Application Rules until a
successful match is made and the rule is applied. If no matches are made, then no rule will be applied to the application, and it will run as
normal.
Endpoint Privilege Management for Mac must match every definition you configure before it will trigger a match. The rules are combined
with a logical AND.
Application definitions requiring a match can also be negated. To target applications that do not match the definition, select does NOT
match from the dropdown.
Application Requests Authorization
The application requires authorization, so you need to approve that request. This applies to anything in macOS that has a padlock on the
dialog box or where the system requires authorization to change something. The URIs are unique to the application. The Auth Request
URIs are generic and any Auth Request URIs can be requested by any application.
When an application triggers an authorization request, the application will use a unique Auth Request URI. This URI will be different to the
URI of the application itself. This matching criteria allows you to target any authorization request by matching the Auth Request URI,
allowing you to target that specific Auth Request URI and apply your own controls.
This matching criteria can be used in combination with other criteria to target authorization requests from specific applications if more than
one application uses the same Auth Request URI.
When this matching criteria is used in a definition, it will only match the authorization request of the application, and not the execution of
the application. If you want to apply rules to both the application execution and application authorization request, then separate definitions
must be created for each.
If you want to apply different rules to application execution and application authorization requests, then definitions must be added to
different Application Groups and applied to different Application Rules.
Mac Packages are always configured to match exactly against the system.install.software request URI. You cannot set Auth Request
URI or Perform Match Using options.
This matching criteria can be used with the following application types:
l
Binaries
l
Bundles
l
Packages
l
System Preferences
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
43
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Command Line Arguments
The Command Line Arguments matching criteria allows you to target a binary or sudo command based on the arguments passed to the
command being executed on the command line. Command Line Arguments can be executed either through the Terminal, or through a
script. With this matching criteria, you can apply a specific action (such as block, allow, or audit) to specific Command Line Arguments,
rather than only applying actions to the use of the binary or sudo command.
The Command Line Arguments matching criteria will match specifically the arguments passed to the binary or sudo command. The
following example shows a command for listing the contents of the /Applications directory:
MyMac:~ standarduser$ ls -la /Applications
l
ls is the binary being executed, and is targeted by using the File or Folder Name matching criteria in a Binary definition.
l
-la /Applications are the arguments being passed to ls, and is targeted by using the Command Line Arguments matching criteria
in a Binary definition.
Note: Endpoint Privilege Management for Mac will only match the command line arguments, which will not include the
beginning binary or sudo command being executed. If you want to match both the binary and sudo command, as well as the
command line, then both the File or Folder Name and the Command Line Arguments matching criteria must be enabled and
populated in the definition.
This matching criteria allows you to target all, or just parts of the command line being used. This is achieved by inserting wildcards into the
Command Line Arguments string, defining which part of the command line you want to match, or by using a regular expression.
This matching criteria includes the following matching options:
l
Command Line Arguments (for example, -la /Applications)
l
Exact Match
l
Starts With
l
Ends With
l
Contains
l
Regular Expressions
This matching criteria can be used with the following application types:
l
Binaries
l
Scripts
l
Sudo Commands
Note: You can match on any command line argument with the exception of those listed in "Mac Sudo Command Arguments
Not Supported" on page 28.
File or Folder Name Matches
This matching criteria allows you to target applications based on their name / path on disk. It is an effective way of automatically
allowlisting applications located in trusted areas of the filesystem (for example, /Applications or /System), and for targeting specific
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
44
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

applications based on their full path.
This matching criteria can be used in combination with other criteria in a definition, giving you more granularity over which applications you
can target based on their properties. Although you may enter relative file names, we strongly recommended you enter the full path to a file.
Applications can be matched on the file or folder name. You can choose to match based on the following options:
l
File or Folder Name (for example, /Applications/iTunes.app)
l
Exact Match
l
Starts With
l
Ends With
l
Contains
l
Regular Expressions
You can match on the file path containing or starting with the /AppTranslocation/ folder, however we recommend you block all
applications attempting to run from this location to ensure unsigned applications are not run. Instead, we recommend you run applications
from the /Applications/ folder.
Note: Targeting bundles with an Exact Match path applies only to the main binary in the Contents/MacOS directory as
specified in the bundle's plist.
This matching criteria can be used with the following application types:
l
Binaries
l
Bundles
l
Packages
l
System Preferences
l
Sudo Commands
l
Scripts
File Hash (SHA-1 Fingerprint)
This definition ensures the contents of the application (which can normally be edited by any user) remain unchanged, as changing a single
character in the script will cause the SHA-1 hash to change.
A file hash is a digital fingerprint of an application, generated from the contents of application binary or bundle. Changing the contents of
an application results in an entirely different hash. Every application, and every version of the same application, has a unique hash.
Endpoint Privilege Management for Mac uses hashes to compare the application being executed against a hash stored in the
configuration.
File hash matching is the most specific criteria, as it can be used to ensure the application being run is the exact same application used
when creating the definition, and that it has not been modified.
This matching criteria includes the following matching options:
l
File Hash
This matching criteria can be used with the following application types:
l
Binaries
l
Bundles
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
45
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Packages
l
System Preferences
l
Sudo Commands
l
Scripts
Note: Although file hash is the more reliable matching criteria for matching a specific application, you must ensure definitions
are kept up to date. When updates are applied to the endpoint, new versions of applications may be added, and so their SHA-1
hashes will be different. Applications on different versions of macOS also have different SHA-1 hashes.
Changes to File Hash Auditing
Prior to version 21.6, the file hash audited depends on the context, for example, whether the application is a bundle or whether it’s code
signed:
l
Signed applications report the code directory hash (CDHash).
l
Unsigned single files (binaries, scripts) and signed packages report a SHA-1.
l
Unsigned bundles report a recursively generated SHA-1 of all their contents. In a worst case scenario, this can take several
minutes to generate.
In version 21.6, what is audited is simplified to provide support for reputation services such as VirusTotal:
l
Single files report a SHA-1.
l
Bundles report the SHA-1 of their main binary, as specified by their Info.plist.
Changes to File Hash Matching Criteria
Support for matching signed applications using their CDHash is continuing, and we also now support matching against the audited SHA-1.
Support for recursive SHA-1 matching for unsigned bundles will be removed once Apple Silicon is widely adopted by businesses, as
unsigned code is not allowed to run on these devices. It can cause significant performance issues.
How to Determine a File’s Hash for Matching Criteria
If you have audit events available through reporting, then you can find the appropriate SHA-1 file hash there. This is not as secure as using
a CDHash for bundles.
Signed application (bundle, binary, script):
codesign -dvvv <path to bundle or file> 2>&1 | egrep "^CDHash"
Unsigned files (binary, script) and both signed and unsigned packages:
shasum -a 1 <path to file>
Unsigned bundle:
shasum -a 1 <path to bundle’s main binary>
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
46
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

File Hash (SHA-256) Matches
Set the SHA-256 file hash on an application. The SHA-256 hash is supported on all appropriate macOS applications. On the macOS
operating system, you can select match. The does NOT match setting is not available on macOS. We recommend using SHA-256 rather
than SHA-1.
How to Determine a File’s Hash for Matching Criteria
If you have audit events available through reporting, then you can find the appropriate SHA-256 file hash there. This is not as secure as
using a CDHash for bundles.
Unsigned files (binary, script) and both signed and unsigned packages:
shasum -a 256 <path to file>
Unsigned bundle:
shasum -a 256 <path to bundle’s main binary>
File Version Matches
If the application you entered has a File Version property, then it is automatically extracted. You can choose to Check Min Version,
Check Max Version, and edit the version number fields. Alphanumeric characters are supported in the version of applications.
For application types with defined versions, you can optionally use the File Version matching criteria to target applications of a specific
version or range of versions. This allows you to apply rules and actions to certain versions of an application, for example, blocking an
application if it’s version is less than the version defined in the definition.
File Version matching can be applied either as a minimum required version, as a maximum required version, or you can use both to define
a range of versions (between a minimum and a maximum).
This matching criteria includes the following matching options:
l
File Min Version
l
File Max Version
This matching criteria can be used with the following application types:
l
Bundles
l
System Preferences
Parent Process Matches
This option can be used to check if an application’s parent process matches a specific Application Group. You must create an Application
Group for this purpose or specify an existing Application Group in the Parent Process group. Setting match all parents in tree to True will
traverse the complete parent and child hierarchy for the application, looking for any matching parent process. Setting this option to False
only checks the application’s direct parent process.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
47
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

When a new application executes, it is executed by another process, or parent process. In most cases on macOS, the parent process will
be launchd. However, sometimes applications like binaries and bundles are executed by other applications. For example, binaries like
curl can be executed from Bash, and will be created as a child of the Terminal process. However, curl can also be used by applications.
The Parent Process matching criteria allows you to the target applications based on their parent process, so you can apply different rules
and actions depending on where the application is being executed from. In the example above, you can use Parent Process matching to
allow curl to be used by an authorized application, but still block users from executing it directly in the Terminal.
Parent Processes are defined as an Application Group, so you can identify multiple parents without having to create multiple definitions.
This also means the parent process can be defined as any type of application (binary, bundle, system preference, or package) using any
of the relevant matching criteria for each application.
This matching criteria includes the following matching options:
l
Parent Process Group (dropdown menu of all Application Groups existing in the configuration)
This definition can be used with the following application types:
l
Binaries
l
Bundles
l
Sudo Commands
l
Scripts
Publisher Matches
This option can be used to check for the existence of a valid publisher. If you have browsed for an application, then the certificate subject
name will automatically be retrieved, if the application has been signed. By default, a substring match is attempted (Contains).
Alternatively, you may choose to pattern match based on either a wildcard match (? and *) or a Regular Expression. The available
operators are identical to the File or Folder Name definition.
Some applications are digitally signed with a certificate, giving a guarantee the application is genuine and from a specific vendor. The
certificate also ensures the application has not been tampered with by an unauthorized source. The vendor who owns the certificate can
be identified from certain properties of the certificate, which are referred to as Authorities. A certificate typically contains several
Authorities linked together in a chain of trust.
To check if an application has been digitally signed and what the certificate Authorities are, use the following command example to check
the certificate of the iTunes.app application bundle:
Codesign -dvvv /Applications/iTunes.app/
If the application has a certificate, there will be one or more Authorities listed in the output:
Authority=Software Signing
Authority=Apple Code Signing Certification Authority
Authority=Apple Root CA
In the output, the first Authority listed is the authority most specific to the application. In this example, you can see Apple uses the
certificate Authority Software Signing to digitally sign iTunes.app.
With the Publisher matching criteria, you can target applications based on the publisher information contained in its certificate. This
matching criteria can also be used in combination with other matching criteria, as a way of ensuring the application is a genuine
application from the vendor.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
48
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Note: All apps downloaded from the Apple Store will have certificates with the same authority, as Apple resigns all
applications before making them available in the Apple Store.
This matching criteria includes the following matching options:
l
Publisher (For example, the Publisher for Apple applications is Software Signing)
l
Exact Match
l
Starts With
l
Ends With
l
Contains
l
Regular Expressions
This definition can be used with the following application types:
l
Binaries
l
Bundles
l
Packages
l
System Preferences
l
Sudo Commands
Source
If an application was downloaded using a web browser, this option can be used to check where the application or installer was originally
downloaded from. The application is tracked by Endpoint Privilege Management for Mac at the point it is downloaded, so if a user decided
to run the application or installer at a later date, the source can still be verified. By default, a substring match is attempted (Contains).
Alternatively, you can choose to pattern match based on either a wildcard match (? and *) or a Regular Expression. The available
operators are the same as the File or Folder Name definition.
This definition can be used with the following application types:
l
Bundles
l
System Preferences
URI
Every macOS application bundle has a defined Uniform Resource Identifier (URI), a property that uniquely identifies the application to the
system. URI’s follow a specific structure, typically referencing the vendor and application. For example, the URI for Apple iTunes is
com.apple.iTunes.
The URI matching criteria provides an effective way of targeting applications where the filename or file path may not always be known. It is
also an effective way of targeting applications from a specific vendor.
This matching criteria can also be used in combination with other matching criteria, as a way of ensuring the application is a genuine
application from the vendor.
This is the Unique Request Identifier for the application bundle. You can choose to match based on the following options:
l
URI (for example, com.apple.iTunes)
l
Exact Match
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
49
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Starts With
l
Ends With
l
Contains
l
Regular Expressions
This definition can be used with the following application types:
l
Bundles
Install Action Matches
This definition can be used to allow installation of bundles to the /Applications directory. This matching criteria can be used in
combination with other criteria to allow or deny installation of the matched bundle.
You can choose from the following options to allow installation to the /Applications directory:
l
Yes
l
No
This definition can be used with the following application type:
l
Bundles
Delete Action Matches
This definition can be used to allow deletion of bundles from the /Applications directory. This matching criteria can be used in
combination with other criteria to allow or deny deletion of the matched bundle.
You can choose from the following options to allow deletion from the /Applications directory:
l
Yes
l
No
This definition can be used with the following application type:
l
Bundles
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
50
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Manage Disk Mounted Images
Endpoint Privilege Management for Mac examines each Disk Mounted Image (DMG) when running with a valid license. If there are one or
more bundles of applications in the Disk Image, where the policy is contained within an allow rule for the Workstyle, and the install action
is also set to Yes in the Application Rule, the user is allowed to copy those bundles to the System Applications folder on the endpoint.
If the applications do not have an Endpoint Privilege Management Allow rule, the copying of the bundle defaults to normal macOS
functionality where admin credentials are required to copy the bundle to the System Applications folder. Standard macOS functionality is
used if anything other than an Allow rule is associated with the application bundle in the DMG, such as Block or Passive.
Note: Previously, to trigger copy functionality, the bundle from the DMG had to be in an Application Group with an Endpoint
Privilege Management Allow rule. As of version 5.4, the same condition applies, however, the bundle must also have Install
Action match set to Yes in the Application matching criteria, within the Application Groups settings to right-click and Install
with Defendpoint. Existing policies must be altered to reflect the changes in functionality.
For more information, see "Manage System Applications" on page 54.
Configure the defendpoint.plist File
Managing DMGs is controlled by default, but it can be turned off by editing the defendpoint.plist file.
The location for the defendpoint.plist file is /Library/Application Support/Avecto/Defendpoint/defendpoint.plist.
Set the MountAssistant key to false to turn off the Endpoint Privilege Management for Mac management of DMG files (it is set to true by
default):
<key>MountAssistant</key>
<false/>
You must restart the defendpointd daemon after you edit the defendpoint.plist file for any changes to take effect. This can either be
done by restarting the machine or by running these commands from Terminal:
sudo launchctl unload /Library/LaunchDaemons/com.avecto.defendpointd.plist
sudo launchctl load /Library/LaunchDaemons/com.avecto.defendpointd.plist
Note: If you specify the -w parameter in the command line, it will disable the daemon and a reboot will not turn it back on. Not
including the parameter will allow the daemon to restart after a reboot of the endpoint.
Format of Messages
Within the defendpoint.plist file, you can also modify the string used for the messaging in the key tag.
The format of the messages is a key and string tag:
<key>MountMessageAllow</key>
<string>Allow copying "[APP_NAME]" from "[MOUNT_NAME]" to Applications?</string>
The following placeholders can be used:
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
51
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
[APP_NAME]: Replaced by the Application Name.
l
[MOUNT_NAME]: Replaced by the Volume Name of the mounted DMG.
When you enter your own strings for the above keys, the formatting is 'what you see is what you get'. For example, if you press Enter, then
you will get a new line.
You can configure the message displayed to the user at the endpoint in the following scenarios:
l
MountMessageAllow: Message that appears when a DMG containing an allowed bundle, is mounted.
l
MountMessageNoteSame: Message that appears in smaller text below the MountMessageAllow message if the bundle is
allowed, but the same version exists in the destination.
l
MountMessageNoteNewer: Message that appears in smaller text below the MountMessageAllow message if the bundle is
allowed but a newer version of the bundle exists in the destination.
l
MountMessageNoteOld: Message that appears in smaller text below the MountMessageAllow message if the bundle is allowed
but an older version of it exists in the destination.
l
MountNotificationSuccess: Message that appears in the macOS notification center when the copying process succeeds.
l
MountNotificationFailure: Message that appears in the macOS notification center when the copying process fails.
If the message keys above have not been set, Endpoint Privilege Management for Mac uses the default values and strings. If you enter
the <key> but do not specify the <string>, then the message will be empty.
You must use escaped characters for valid XML, such as in the examples below:
Symbol Escaped Form
" ""
& &"
‘ &apos"
< <"
> >"
Example: The following examples show sample messages in the defendpoint.plist file.
<key>MountMessageAllow</key>
<string>Allow copying "[APP_NAME]" from "[MOUNT_NAME]" to Applications?</string>
<key>MountMessageNoteSame</key>
<string>Note: same version of the item named "[APP_NAME]" already exists in this
location.</string>
<key>MountMessageNoteNewer</key>
<string>Note: a newer version of the item named "[APP_NAME]" already exists in this
location.</string>
<key>MountMessageNoteOlder</key>
<string>Note: an older version of the item named "[APP_NAME]" already exists in this
location.</string>
<key>MountNotificationSuccess</key>
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
52
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

<string>"[APP_NAME]" was successfully copied from "[MOUNT_NAME]" into the Applications
older.</string>
<key>MountNotificationFailure</key>
<string>"[APP_NAME]" was not successfully copied from "[MOUNT_NAME]" into the
Applications folder.</string>
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
53
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
Manage System Applications
Endpoint Privilege Management for Mac examines each application and, if there is an application bundle where the application is
associated with an Allow rule and Install Action match of Yes, the user can right-click the application and select Install with Privilege
Management. This will install the bundle in the /Applications folder on the endpoint.
If the applications do not have an Allow rule with an Install Action match or Delete Action match of Yes, the management of the bundle
defaults to normal macOS functionality where admin credentials are required to manage the bundle in the /Applications folder. Standard
macOS functionality is used if anything other than an Allow rule with an Install Action match or Delete Action match of Yes is
associated with the application bundle, such as Block or Passive.
Note: You cannot use File Hash matching criteria to install or uninstall unsigned bundles.
Note: Per system functionality, applications that are running or protected by System Integrity Protection (SIP) cannot be
uninstalled.
For more information, see the following:
l
"Install Action Matches" on page 50
l
"Delete Action Matches" on page 50
Manage the Endpoint Privilege Management Finder Extension
To use Run with Privilege Management menu functionality to manage the System Applications folder, the Privilege Management
Finder Extension must be enabled under System Preferences > Extensions > Finder Extensions.
The Finder extension allows end users to install applications. The extension works in the same way as the native macOS functionality.
The following sections provide details on the Finder extension behavior.
Remove Applications From the /Applications Folder
Standard users can drag an application from the /Applications folder to the Trash.
l
If the application matches a policy entry which has Deletable set on it, then any messages configured in the policy are displayed
first to the user, and the user can proceed.
l
If the policy does not contain a matching entry for the item being removed, then this is treated as a passive event and the user is
prompted for an administrative user’s credentials to proceed.
Install Applications Distributed in a DMG File
The Finder extension is active within mounted DMG volumes to install applications.
As with all previous releases, if a standard user attempts to drag an application to the /Applications folder, then they are prompted for an
administrator’s user name and password to proceed.
Allowing standard users to install applications using the Finder extension or MountAssist features remains, as per previous releases.
VLC media player is an example of an application distributed in a DMG volume.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
54
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Install Applications Distributed from a non-DMG File
As of version 22.7, a standard user can drag files to the /Applications folder to install applications.
This only supports application bundles which are not contained within a mounted disk (DMG).
Standard users can drag an application from the /Applications folder to the Trash.
l
Removing these file types behaves passively if the dragged item does not match any entries in the policy.
l
Allows the user to remove the application pending the completion of any configured Endpoint Privilege Management for Mac
messaging.
Allow Authorization of the Console Application
Note: Starting in version 24.1, this feature is no longer supported.
With the introduction of macOS Big Sur, standard user accounts are required to enter administrator credentials when attempting to stream
logs in the Console application. This behavior does not use Apple's authorization services framework.
To permit standard users access to the Console application, you can create
a policy allowing access to the application from the Finder Extension
context menu. The context menu is not available through the Dock or
Spotlight.
When configured, a standard user can stream logs in the Console
application as an administrator user, which mirrors the behavior of the
Console application on macOS Catalina.
This feature explicitly works for the Console application in
/System/Applications/Utilities/.
Note: The feature is not available for any other application.
Configure the Authorization
Note: Starting in version 24.1, this feature is no longer supported.
Target the Console application in an allow rule with any matching criteria. We recommend using the following:
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
55
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Application type: Bundle
l
Matching criteria:
o
URI: com.apple.console
o
Publisher: Software Signing
Keep the following points in mind when setting up the policy:
l
If you are using a variation of the QuickStart policy for Mac, you might need to add a new rule above the (Default) Passive -
System Trusted in All Users as the Console application matches within that Application Group.
l
If the allow rule is configured with a message, then the message appears when the user attempts to open the Console application
in a traditional method. We recommend using an allow rule without a message so that the users can use the feature without being
prompted.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
56
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Insert a Binary
Note: Matching criteria is case sensitive.
1. Select the Application Group you want to add the binary control to.
2. Right-click and select Insert Application > Binary.
3. Enter a File or Folder Name, or click Template to choose a template.
4. Enter a description or accept the default and click Next . You can leave the Description blank to match on all binaries.
5. You must configure the matching criteria for the binary. You can configure:
l
File or Folder Name matches
l
File Hash (SHA-1 Fingerprint)
l
File Hash (SHA-256) matches
l
Application Requests Authorization
l
Command Line Arguments
l
Publisher matches
l
Parent Process matches
6. Click Finish. The binary is added to the Application Group.
For more information, see the following:
l
"File or Folder Name Matches" on page 44
l
"File Hash (SHA-1 Fingerprint)" on page 45
l
"Application Requests Authorization" on page 43
l
"Command Line Arguments" on page 44
l
"Publisher Matches" on page 48
l
"Parent Process Matches" on page 47
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
57
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Insert a Bundle
Note: Matching criteria is case sensitive.
1. Select the Application Group you want to add the bundle control to.
2. Right-click and select Insert Application > Bundle.
3. Enter a File or Folder Name, or click Template to choose a template.
4. Enter a description or accept the default and click Next . You can leave the Description blank to match on all bundles.
5. You must configure the matching criteria for the bundle. You can configure:
l
File or Folder Name matches
l
File Hash (SHA-1 Fingerprint)
l
File Hash (SHA-256) matches
l
Source
l
File Version matches
l
URI
l
Application Requests Authorization
l
Publisher matches
l
Parent Process matches
6. Click Finish. The bundle is added to the Application Group.
For more information, see the following:
l
"File or Folder Name Matches" on page 44
l
"File Hash (SHA-1 Fingerprint)" on page 45
l
"Source" on page 49
l
"File Version Matches" on page 47
l
"URI" on page 49
l
"Application Requests Authorization" on page 43
l
"Publisher Matches" on page 48
l
"Parent Process Matches" on page 47
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
58
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Insert a Package
Note: Matching criteria is case sensitive.
1. Select the Application Group you want to add the package to.
2. Right-click and select Insert Application > Package.
3. Enter a File or Folder Name, or click Template to choose a template.
4. Enter a description or accept the default and click Next. You can leave the Description blank to match on all packages.
5. You must configure the matching criteria for the package. You can configure:
l
File or Folder Name matches
l
File Hash (SHA-1 Fingerprint)
l
File Hash (SHA-256) matches
l
Application Requests Authorization
l
Publisher matches
6. Click Finish. The package is added to the Application Group.
For more information, see the following:
l
"File or Folder Name Matches" on page 44
l
"File Hash (SHA-1 Fingerprint)" on page 45
l
"Application Requests Authorization" on page 43
l
"Publisher Matches" on page 48
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
59
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Insert a Script
Use the Script application type to target a script that is trying to run privileged operations using sudo. System administrators can apply
Application Rules on scripts to allow installation and management of development tools; for example, Homebrew.
Supported script types include:
l
bash (.sh)
l
ruby (.rb)
l
python (.py - xattr)
Note: Matching criteria is case sensitive.
1. Select the Application Group you want to add the script control to.
2. Right-click and select Insert Application > Script.
3. Enter a File or Folder Name.
4. Enter a description or accept the default and click Next. You can leave the Description blank to match on all scripts.
5. You must configure the matching criteria for the binary. You can configure:
l
File or Folder Name matches
l
File Hash (SHA-1 Fingerprint)
l
File Hash (SHA-256) matches
l
Command Line Arguments
l
Parent Process matches
6. Click Finish. The script is added to the Application Group.
For more information, see the following:
l
"File or Folder Name Matches" on page 44
l
"File Hash (SHA-1 Fingerprint)" on page 45
l
"Command Line Arguments" on page 44
l
"Parent Process Matches" on page 47
Install Homebrew
The Homebrew installer is a shell script which users can download to their machine and run. This script internally uses sudo to create
folders on the system and set their ownership/permissions to be accessible by the installing user, reducing the need for further privileged
sudo operations when users want to install packages.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
60
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Allow Standard Users to Install Homebrew vian Endpoint Privilege Management
for Mac
Prepare a Script
The current installation script for Homebrew must be modified slightly to work with Endpoint Privilege Management for Mac.
To achieve this, create a script that contains the following:
#!/bin/bash
# Download the latest brew install script using curl
curl -fsSL https://raw.githubusercontent.com/Homebrew/install/master/install.sh -o install.sh
# The following command modifies the install.sh script, creating a backup of the original
# as install.sh.bak, and does the following modifications
# - replaces occurrences of "/usr/bin/sudo" with just "sudo" to allow customers using
# the non-Apple sudo to continue
# - Inserts a line "HAVE_SUDO_ACCESS=0" near the top of the file. This bypasses the
# built-in have_sudo_access feature with the expectation that the PMFM plugin policy is
# correctly configured to match this script
sed -i .bak -e $'s^set -u^set -u\\\nHAVE_SUDO_ACCESS=0^' \
-e '/unset HAVE_SUDO_ACCESS/d' install.sh
source install.sh
rm install.sh
rm install.sh.bak
Check the shasum of the file you created to ensure no copy and paste irregularities have introduced differences.
To check the shasum of the script, run the following command in Terminal:
shasum -a 1 <name of script>
Add the Script to Policy
To create a rule to match this script in the Policy Editor:
1. Create an Application Group to add the script control.
2. Right-click and select Insert Application > Script.
3. Enter * as the file or folder name, as you're matching explicitly on hash.
4. Enter a description of User Homebrew Installation.
5. Set the File Hash to value <insert shasum here>.
Ensure this file hash is the same as the script you prepared earlier, in case you made any custom modifications.
6. Click Finish. The script is added to the Application Group.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
61
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Add a sudo Command for Homebrew to Policy
In the same Application Group:
1. Right-click and select Insert Application > Sudo Command.
2. Enter * to represent any sudo command.
3. Enter a description or accept the default, and click Next.
4. Configure the Parent Process Matches to be the group which you are editing.
This keeps the configuration of Homebrew isolated within the policy and easier to navigate. Alternatively, you can separate the
Script and Sudo application definitions.
5. Click Finish. The sudo command is added to the Application Group.
Set Up an Application Rule for Homebrew
1. Select the Workstyle that is appropriately filtered for users you want to allow to install Homebrew.
2. Create an application assignment for the Application Group that contains the sudo command, of type Allow Execution, with your
messaging and auditing preferences.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
62
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Insert a Sudo Command
Note: Matching criteria is case sensitive.
1. Select the Application Group you want to add the sudo command to.
2. Right-click and select Insert Application > Sudo Command.
3. Enter a File or Folder Name, or click Template to choose a template.
4. Enter a description or accept the default and click Next. You can leave the Description blank to match on all sudo commands.
5. You can leave the Description blank to match on all sudo commands.
6. You must configure the matching criteria for the sudo command. You can configure:
l
File or Folder Name matches
l
File Hash (SHA-1 Fingerprint)
l
File Hash (SHA-256) matches
l
Command Line Arguments
l
Publisher matches
l
Parent Process matches
7. Click Finish. The sudo command is added to the Application Group.
For more information, see the following:
l
"File or Folder Name Matches" on page 44
l
"File Hash (SHA-1 Fingerprint)" on page 45
l
"Command Line Arguments" on page 44
l
"Publisher Matches" on page 48
l
"Parent Process Matches" on page 47
Sudo Switches
Endpoint Privilege Management for Mac supports running sudo commands with the following switches:
l
-b, --background
l
-e, --edit
l
-i, --login
l
-S, --stdin
l
-s, --shell
l
-V, --version
When a sudo command is run, Endpoint Privilege Management for Mac ignores any switches that have been used and will match the rest
of the command against the application definition. If Endpoint Privilege Management for Mac matches against a rule that allows execution,
the sudo command runs with any supported switches that were used. Any switches that are not supported by Endpoint Privilege
Management for Mac are ignored.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
63
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

If Endpoint Privilege Management for Mac matches on a passive rule or doesn't match any rules, then the sudo command runs with any
supported or unsupported switches that have been used.
Note: Th -e switch requires configuration in Endpoint Privilege Management for Mac for it to be supported. For more
information, see "Edit -e Switch" on page 64.
Note: The -l --list switch, which lists the commands the user is allowed to run, does not take into account the commands that
are restricted by Endpoint Privilege Management for Mac.
Edit -e Switch
The -e --edit switch, also known as sudoedit, allows the user to edit one or more files using their preferred text editor. The text editor is
defined by setting the SUDO_EDIT, VISUAL, or EDITOR environment variable in the user's Terminal session. Otherwise, the default
editor, Vim, is used. To configure your policy to support the -e switch, you must set up a sudo command Application Rule so that:
l
The File or Folder Name definition is set to sudoedit with the Perform Match Using set to Exact Match.
l
The Command Line Arguments definition is set to the path of the files you want to control using this rule.
For example, the application definition shown in the following screenshot
supports the sudo command sudo -e /etc/hosts.
The audit log will show an application of /usr/bin/sudo and the command line arguments will have -e prepended to them.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
64
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Insert a System Preference Pane
Note: Matching criteria is case sensitive.
IMPORTANT!
When adding the Battery preference pane to a policy, the match must include the URI and exact file path, similar to:
Failing to configure the preference correctly can result in matching unrelated authorization requests, which can lead to unexpected
behavior.
Add a System Preference Pane
1. Select the Application Group you want to add the system preference pane to.
2. Right-click and select Insert Application > System Preference Pane.
3. Enter an Auth Request URI or click Template to choose a template.
4. Enter a description or accept the default and click Next. You can leave the Description blank to match on all bundles.
5. You must configure the matching criteria for the system preference pane. You can configure:
l
File or Folder Name matches
l
File Hash (SHA-1 Fingerprint)
l
File Hash (SHA-256) matches
l
Source
l
File Version matches
l
Application Requests Authorization
l
Publisher matches
6. Click Finish. The System Preference Pane is added to the Application Group.
For more information, see the following:
l
"File or Folder Name Matches" on page 44
l
"File Hash (SHA-1 Fingerprint)" on page 45
l
"Source" on page 49
l
"File Version Matches" on page 47
l
"Application Requests Authorization" on page 43
l
"Publisher Matches" on page 48
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
65
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Insert Applications from Templates
Application templates provide a simple way to pick from a list of known applications. A standard set of templates are provided that cover
basic administrative tasks.
There are two ways you can insert applications into Application Groups. If you want to insert multiple applications from the BeyondTrust
templates, you must add the applications from the template menu.
Use the Add Apps to Template Menu
1. Select the Application Group you want to add the application to.
2. Right-click and select Insert Application > Application Template. Choose one or more applications to add to the Application
Group. You can select multiple rows using standard Windows functionality.
3. Click Insert to add the applications.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
66
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Messages
You can define any number of end user messages. Messages are displayed when a user’s action triggers a rule (application, sudo, or
package installers). Rules can be triggered by an application launch, block, or when content is modified.
Messages provide an effective way of alerting the user before an action is performed. For example, before elevating an application or
advising an application launch.
Messages give the user information about the application or content, the action taken, and can be used to request information from the
user. Messages also allow authorization and authentication controls to be enforced before access to an application is granted.
Messages are customizable with visual styles, corporate branding, and display text, so you are offered a familiar and contextual
experience. Messages are assigned to Application Rules. A message will display different properties depending on which of these targets
it is assigned to. To view the differences, a Preview option allows you to toggle between the Application Preview and the Content
Preview. This is available from the Preview dropdown menu located in the top-right corner of the details pane.
Once defined, a message may be assigned to an individual rule in the Workstyles Rules tab by editing the rule. Depending on the type of
Workstyle you’ve created, Endpoint Privilege Management for Mac may auto-generate certain messages for you to use.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
67
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Create Messages
To create a message:
1. Select the Messages node in the relevant Workstyle. The right-hand pane displays the All Messages page.
2. Right-click and click New Message.
3. Select a message template from the first dropdown. You can choose from:
l
Allow Message (Audit)
l
Allow Message (enter Reason)
l
Allow Message (Select Reason)
l
Allow Message (with Authentication)
l
Allow Message (with Challenge)
l
Block Message
l
Request Message (enter Reason)
l
Request (Select Reason)
4. You can change the other options if required to customize it to your business.
5. If you select the check box Show the details of the application being executed the Program Name, Program Publisher, and
Program Path names and variables are hidden from the preview and the message displayed on the endpoint.
6. Click OK to finish creating your message.
A new message will be created. You may now further refine the message by selecting it and editing the Design and the Text options
available beneath each message.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
68
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Multi-factor Authentication using an Identity Provider
Multi-factor authentication (MFA) using an identity provider can be configured for messages in Endpoint Privilege Management. Identity
providers supported by Endpoint Privilege Management include those using OpenID Connect (OIDC) protocol.
In Endpoint Privilege Management, messages can be designed with a combination of authentication and authorization settings.
l
Authentication: MFA with an identity provider, user credential, and smart card
l
Authorization: Challenge / response authorization
Authentication and Authorization Groupings in Endpoint Privilege Management
Groupings support and/or logic.
l
Groupings by authentication: Setting more than one way the end user can authenticate which can include the typical
authentication methods (user credential, designated user, and smart card) and MFA with an identity provider.
In the Message Designer, pair Step 1a - User Authentication with Step 1b - Multifactor Authentication. This can be and/or
configuration.
l
Groupings by authentication and authorization: Authentication methods paired with authorization always use or logic.
Authorization applies an additional challenge / response layer to the end user accessing an application. The challenge / response
provides an alternative to MFA authentication if that method is unavailable (for example, the browser is unavailable or the end user
phone is not available).
Here are some grouping scenarios:
l
MFA and Designated User or challenge / response: The end user must successfully respond to all authentication prompts to
access an application. Challenge / response is optional.
l
MFA or Designated User or challenge / response: The end user must successfully enter either MFA or Designated User
credentials. Challenge / response is optional.
l
MFA and User authentication or challenge / response: The end user must successfully respond to all authentication prompts to
access an application. Challenge / response is optional. When this authentication is combined, the Step 1c - Authentication
Grouping is automatically set to and logic.
l
MFA or None as the Authentication Type or challenge / response: The end user must access the application through the identity
provider or challenge / response method.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
69
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Workflow
The workflow depends on the combination of settings configured on the
Message Design page. In the following screen capture, the authentication
and authorization methods are joined with or logic.
The end user must click the link which opens the default browser to the
identity provider logon page. The end user must successfully authenticate
with the identity provider then return to the Confirm Operation dialog box
to enter the user credential. Challenge / response codes are optional.
Add an Identity Provider
You can configure the identity provider in the following places:
l
Endpoint Privilege Management Settings node
l
Messages node
Identity provider configuration is a global setting and applies to all messages.
To add the identity provider:
1. Expand the Windows node or OS X node.
2. Right-click Messages > Set Idp Authentication.
3. Click the relevant tab for the authentication protocol required by your Identity Provider (OIDC or RADIUS).
4. Enter the identity provider details:
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
70
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
OIDC Settings
o
Authority URI: The address of your identity provider.
o
Client ID: Must match the same value configured for your
identity provider's BeyondTrust application.
o
Redirect URI: Must match the same value configured for
your identity provider's BeyondTrust application. The format
is http://127.0.0.1:port_number, where port_number is an
open port on your network. The port_number is only needed
if required by your identity provider. For macOS messages,
enter the static redirect URI for messages to work correctly:
com.beyondtrust.pmfm://idp
l
RADIUS Settings
o
Authentication Mechanism: The authentication type that
is required by your RADIUS server. Supported
authentication mechanisms are MS-CHAPV2 or PAP.
o
Host: The hostname of your RADIUS server.
o
Port: The port number for connecting to your RADIUS
server.
o
Shared Secret: The secret key required by your RADIUS
server.
You can also configure the identity provider on the Message Design page.
Add the Endpoint Privilege Management Application to Microsoft, Okta, or Ping
Identity
The procedures in this section are specific to OIDC implementations.
Create an App Registration
Login to your Azure portal https://portal.azure.com.
Note: Microsoft can change functionality at any time. The screen captures in the following procedure were accurate at the time
of writing.
1. Navigate to your Microsoft Entra ID.
2. Click App registrations.
3. Select New registration.
4. Enter a name for your app registration. Use a name related to Endpoint Privilege Management.
5. Click Register.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
71
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

6. Copy and note your Application (Client) ID for use in the Policy
Editor later.
7. Click Add a Redirect URI.
8. Click Add a platform.
9. Select Mobile and Desktop Applications.
10. Add a Custom Redirect URIs and set the value to:
http://127.0.0.1
11. Click Configure.
12. Go back to your newly created app registration.
13. Click Endpoints. The endpoints display on the right.
14. Copy the value from the OpenID Connect metadata
documentbox. Only this part of the URL is required:
https://login.microsoftonline.com/87549b3f-a6ba-4ca4-9d99-
ff2944ac4234/v2.0
The configuration is now complete. The following values are required to configure the IdP in the Endpoint Privilege Management Policy
Editor for both Windows and macOS.
l
Authority URI: The value copied in step 14.
l
Client ID: Application (Client) ID from step 6.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
72
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Redirect URI: Custom redirect URIs set in step 10.
Enforce MFA For Every Logon Attempt
In Entra ID, you might want users to always go through the multi-factor authentication process every time they try to access an application
in a rule (if multi-factor authentication is configured in the message).
For more information, see the BeyondTrust Knowledge Base article, Using Additional Scopes and max_age to enforce
always-auth with messages in Azure AD.
Add Endpoint Privilege Management to Okta
1. Start your Okta instance.
2. Click Create App Integration.
3. In the Create a new app integration section, select OIDC - OpenID Connect.
4. Select Native Application as the application type.
5. Select Authorization code for the Grant type.
6. Add the sign-in and sign-out URIs.
l
Sign-in redirect URI: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signin-oidc
l
Sign-out redirect URI: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signout-callback-oidc
7. Select the controlled access applicable to your organization, and then click Save.
After you add EPM to Okta, you can get the information you need to set up the OpenID Connect authentication.
8. Go to the application instance for Endpoint Privilege Management.
9. Select General Settings, and then click Edit.
10. For the EPM OpenID Connect Setup Wizard, you need to copy the following information from the Edit page:
l
Domain: Prefix the protocol HTTPS://
l
Client ID
l
Client Secret
Note: Confirm the domain name configured in Okta. This domain name might be different than the domain configured for your
email address. For example, while the domain managed in Okta might be domain.com, the email address might be
[email protected]. Both pieces of information are required.
11. You can now visit the set-up URL and enter the domain, client ID, and client secret information.
Add Endpoint Privilege Management to Ping Identity
Note: We currently support PingOne, the SaaS service from Ping Identity.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
73
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

1. Start your Ping Identity instance.
2. In the menu, click Connections, and then click Applications.
3. At the right of the Applications title, click the plus sign (+) to add an application.
4. Enter a name for the application (required), and then add a short description (optional).
5. Select OIDC Web App and click Save.
6. Click the Configuration tab.
7. To edit the configuration, click the pencil/edit icon.
8. Under Redirect URLs, click + Add, and then add the sign-in and sign-out URLs. If you are modifying an existing instance, you
might need to open the General section dropdown first.
l
Sign-in redirect URL: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signin-oidc
l
Sign-out redirect URL: https://{dns}-services.pm.beyondtrustcloud.com/oauth/signout-callback-oidc
9. Under Token Endpoint Authentication Method, select Client Secret Post, and then click Save.
10. Click the Resources tab.
11. To edit the resource, click the pencil/edit icon.
12. In the Scopes list, click the + next to profile openID to add it to the Allowed Scopes. You can also filter the list of options by
OpenID to access this option.
13. Click Save.
14. To close the panel, at the top right of the Edit panel, click the X.
15. At the right of the new application entry, toggle the switch to on to give access to users.
16. Click the Configuration tab again. For the EPM OpenID Connect set-up wizard, you need to copy the following information from
the Configuration page.
The Ping identify provider (IdP) configuration is now complete. The following values are required to configure the IdP in the Endpoint
Privilege Management Policy Editor for both Windows and macOS.
l
Issuer: Prefix the protocol HTTPS://
l
Client ID
l
Client secret
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
74
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Message Name and Description
You can change the name and description of a message by right-clicking on the message and selecting Rename or Properties
respectively.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
75
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Message Design
You can configure the following aspects of a message:
l
Message Header Settings
l
User Reason Settings
l
User Authorization
l
Sudo User Authorization
l
Challenge / Response Authorization
As you change the message options, the preview message updates to show you your changes in real-time. Program and content
information is shown with placeholders.
After you configure the message options, you can configure the Message Text, which includes the ability to configure different languages.
The options here are preselected based on the type of message you created but you can override those options if required.
For more information, see "Message Text" on page 81.
Message Header Settings
The message header is highlighted here:
l
Header Style: This is preconfigured; you can choose to remove the header entirely or select from one of the templates provided.
Choose from:
o
No Header
o
Endpoint Privilege Management Header
o
Warning Header
o
Question Header
o
Error Header
l
Show Title Text: This check box is selected by default. You can clear it to remove the text adjacent to the icon if required.
l
Text Color: This controls the color of the text adjacent to the icon. Select the arrow to open the color picker.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
76
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
Background Type: This option controls the color behind the text and icon. If you select Solid, then only Color 1 is available for
you to change. If you select Gradient, then both Color 1 and Color 2 can be configured. If you select Custom Image, then you
can't configure the colors.
l
Custom Image: This section allows you to choose from one of a number of preset custom images or you can click Manage Image
to upload one of your own. The recommended image size is 450 pixels wide and 50 pixels high.
l
Color 1: This option is available if you selected Solid for the Background Type. Select Custom and choose the color you want for
the background.
l
Color 2: This option is available if you selected Gradient for the Background Type. Select Custom and choose the second color
you want for the background. Color 1 is the first color for Gradient backgrounds.
User Reason Settings
You can prompt end users to enter or select a reason in the following scenarios:
l
Before an application launches (Allow Execution message type)
l
Request a blocked application (Block Execution message type)
Configure the following settings:
l
User Reason Type: Select a reason type from the list. Select text box to allow the end user to enter a reason. Select drop-down
to allow the end user to select a preconfigured reason from a list. Select Off if no reason is required from the end user. Configure
messages on the Message Text tab.
l
Remember User Reasons (per-application): Select Yes to cache reasons provided by the end user. A user can then quickly
enter a reason.
Authentication and Authorization Settings
For more information about using authentication and authorization settings, see "Authentication and Authorization Groupings
in Endpoint Privilege Management" on page 69.
Step 1a - User Authentication
l
Authentication Type: Select from None, User must authenticate, or Designated user must authenticate.
o
User must authenticate: Select to force the user to reenter their credentials and confirm they want to run the application.
o
Designated user must authenticate: Select to designate which users can authenticatethe message. Add users from
Designated Users.
l
Password or Smart Card: Select from Any, Password only, or Smart card only. Select Any to allow authentication using
password or smart card / YubiKey authentication. When Password only is selected, a Username and Password field is added to
the message.
l
Designated Users: If you select Designated user must authenticate, click the ... button to add the users who can authenticate
the message.
Note: If you select a method that is not available to the user, then the user cannot authenticate the message.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
77
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Step 1b - Multifactor Authentication
l
Idp Provider: To use an identity provider, select Idp - Yes from the list. If you have not already set up your global identity provider
settings, then you are prompted to add these now.
l
Authentication Context Class References values (acr values): Enter the acr value. The value is optional and required only if
your identity provider uses it.
For more information, see "Add an Identity Provider" on page 70.
Step 1c - Authentication Grouping
l
Requirements: Select a requirement from the list. You can combine authentication methods. The authentication grouping can be
and/or logic. For example, you can require that your users provide both a user name and password and authenticate with an
identity provider. In this case, the end user is required to successfully authenticate with user credentials and with the identity
provider. In the or scenario, the user is required to authenticate using at least one of the authentication methods.
Step 2 - Authorization
You can check the Enabled box for Challenge / Response Authorization to add a challenge code to the message. This check box is
already checked if you selected a challenge message. If you have already created a Workstyle with a challenge message, then the policy
will already have a challenge / response key. Select Change Key and enter a new challenge / response code twice to change it.
l
Challenge Response (C/R): Set this option to C/R - Yes to present the user with a challenge code. The user must enter a
matching response code to proceed. When this option is enabled for the first time, you must enter a shared key. You can click Edit
Key to change the shared key for this message.
l
Authorization Period (per-application): Set this option to determine the length of time a successfully returned challenge code is
active for. Choose from:
o
Once: A persistent challenge code for an application. The code is available until used to authorize the application or the
maximum retries is exceeded (if set). Once authorized, you are allowed to use the application. When you relaunch the
application, you must use a new challenge code.
l
Maximum Attempts: This option determines how many attempts the user has to enter a successful response code for each new
challenge. Set this option to Three Attempts to restrict the user to three attempts, otherwise set this option to Unlimited.
Note: After the third failure to enter a valid response code, the message will be canceled and the challenge code will be
rejected. The next time the user attempts to run the application, they will be presented with a new challenge code. Failed
attempts are accumulated even if the user clicks Cancel between attempts.
Step 3 - User Authentication & Authorization Grouping
l
Requirements: Select a grouping from the list. You can use authentication and authorization settings together, grouped by and/or
logic.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
78
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Sudo User Authorization
You can use the Don't ask for password if already entered dropdown to control how frequently the user has to enter a password to use
the sudo command. This text option is only enabled if the User Authorization has been set to User must authorize or Designated user
must authorize.
The available options are:
l
Ask every time
l
Less than 1 minute ago
l
Less than 5 minutes ago
l
Less than 15 minutes ago
l
Only ask once per session
For more information, see "Challenge / Response Authorization" on page 83.
Image Manager
The Image Manager associated with message creation allows you to Add, Modify, Export, and Delete images referenced in message
headers.
All images are stored inside the Workstyles as compressed and encoded images.
We strongly recommend you delete any unused images to minimize the size of the policies, as Endpoint Privilege Management for Mac
does not automatically delete unreferenced images.
The Image Manager is accessible from the Message Design tab. Click the Manage Images button next to the Custom Image dropdown
menu.
To upload an image:
1. Click Upload Image. The Import Image status dialog box
appears. Click Choose file and browse to the location of the file.
2. Select the image and enter an Image Description. Click OK.
3. The image will be uploaded into Image Manager.
Note: Images must be *.PNG format and be sized between
450x50.
To edit an image:
1. In the Custom Image field, select Manage Images.
2. Select the image in the list and click Edit.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
79
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

3. The Image Properties dialog box appears.
4. Alter the description and click OK.
To delete an image:
1. Select the image in the list and click Delete.
2. When prompted, click Yes to delete the image.
Note: If an image is referenced by any messages, then you will not be allowed to delete it.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
80
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Message Text
After you have made a change to the message text, click Update to see your changes applied to the preview message.
Note: Mac does not support multiple languages.
General
l
Header Message: Controls the text to the right of the icon in the header if it's shown.
l
Body Message: Controls the text at the top of the main message.
Publisher
l
Verification Failure: Controls the text displayed next to the Publisher if the publisher verification fails.
Endpoint Privilege Management for Mac verifies the publisher by checking there is a publisher and also checking the certificate associated
with that publisher is signed. Endpoint Privilege Management for Mac does not check to see if the certificate has been revoked due to the
length of the lookup process that would rely on network connectivity. Instead, Endpoint Privilege Management for Mac relies on the
certificate store to be kept up to date with revoked certificates, which would be a standard operation as the full chain should be in the local
certificate store.
User Reason
Configure the following settings:
l
Reason: Enter the text that displays to indicate a reason is required before the end user can proceed. The Yes button is disabled
until a reason is entered.
l
Reason Error Message: Enter the text displayed to the end user when they fail to select a reason.
l
Drop-down list prompt: Enter the text that displays in the dropdown.
l
User Reason List: To add a custom reason, click the ellipsis (...) button. On the Approved Reasons dialog box, click Add and
enter the reason text. Click OK.
Reason settings can also be applied in sudo policies. The example screen
capture shows a list of reasons. The user must enter the number
corresponding to the reason to proceed.
User Authentication
l
User name: Controls the text adjacent to the field where the user would enter their user name.
l
Password: Controls the text adjacent to the field where the user would enter their password.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
81
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Challenge / Response Authorization
l
Header text: Controls the text that introduces the challenge / response authorization.
l
Hint text: Controls the text in the response code field for challenge / response messages.
l
Information Tip Text: Controls the text above the challenge and response code fields.
Buttons
l
OK Button controls the text displayed on the button that appears on the bottom right.
l
Cancel Button controls the text displayed on the button that appears next to the Yes button.
Depending on the message options, the message box will have either one or two buttons:
l
For an Allow Message (Audit), the message box will have Yes and No buttons.
l
For an Allow Message (enter Reason), the message box will have OK and Cancel buttons.
l
For an Allow Message (with Authentication), the message box will have OK and Cancel buttons.
l
For an Allow Message (with Challenge), the message box will have Authorize and Cancel buttons.
l
For a Block Message, the message box will have an OK button.
l
For a Request Message (enter Reason), the message box will have Submit and Cancel buttons.
You can change the OK Button and Cancel Button text. For instance, you can change it to Yes and No if you are asking the end user a
question.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
82
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Challenge / Response Authorization
Challenge / Response authorization provides an additional level of control for access to applications and privileges, by presenting users
with a challenge code in an end user message. In order for the user to progress, they must enter a corresponding response code into the
message.
Any policy that has a message with challenge / response needs a shared key. This key is defined when you set up the first challenge /
response message in your policy, although you can change it later if required. If you create a Workstyle containing a challenge / response
message or you create a new challenge / response message and you are not prompted to create a shared key, then there is already a
shared key for the policy. You cannot view this shared key, however you can change it here if required.
Challenge / Response authorization is configured as part of end user messages, and can be used in combination with any other
authorization and authentication features of Endpoint Privilege Management for Mac messaging.
Users are presented with a different, unique challenge code each time a challenge / response message is displayed.
Challenge and response codes are presented as an 8 digit number, to minimize the possibility of incorrect entry. When a user is presented
with a challenge code, the message may be canceled without invalidating the code. A new challenge code will be generated every time
the user runs the application.
For more information on configuring challenge / response authorization enabled end user messages, see "Message Design"
on page 76.
Shared Key
The first time you create an Endpoint Privilege Management for Mac end user message with a challenge, you are asked to create a shared
key. The shared key is used by Endpoint Privilege Management for Mac to generate challenge codes at the endpoint.
Once you have entered a shared key, it will be applied to all end user messages that have challenge / response authorization enabled in
the same Endpoint Privilege Management for Mac settings.
To change the shared key:
1. Right-click Endpoint Privilege Management Settings and select Set Challenge / Response Shared Key.
2. In the Challenge / Response Shared Key dialog box, edit the Enter Key and Confirm Key with the new Shared Key.
3. Click OK to complete. If the key entered is not exact, you will be presented with a warning message.
Note: We recommend your shared key is at least 15 characters and includes a combination of alphanumeric, symbolic, upper,
and lowercase characters. As a best practice, the shared key should be changed periodically.
Generate a Response Code
There are two ways to generate a response code. You can either use the PGChallengeResponseUI.exe utility that is installed as part of
the Endpoint Privilege Management Policy Editor, or you can generate them directly within the MMC.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
83
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Note: In order to generate a response code, you must have set a Challenge / Response Shared Key. You are prompted to do
this when you create any policy that has a Challenge / Response message assigned to it. Alternatively, you can set the
Challenge / Response Shared Key from the home page of the Endpoint Privilege Management Settings node by clicking
Set Challenge / Response Shared Key.
You can generate a response code from the Endpoint Privilege Management Policy Editor. This launches a tool called
PGChallengeResponseUI.exe. This tool is part of your installation and can be used independently of the Endpoint Privilege
Management Policy Editor. The tool is installed to the path <Installation Dir>\Avecto\Privilege Guard Endpoint Privilege
Management Policy Editors\.
To generate a response code in the Endpoint Privilege Management Policy Editor:
1. Click the Endpoint Privilege Management Settings node, and then Tools on the right-hand side.
2. Click Response Code Generator.
3. Enter the shared key you have defined and the challenge code from the end user.
4. The response code is generated once both the Shared Key and the 8 character challenge code have been entered.
The response value can then be sent to the end user to enter into their challenge dialog.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
84
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
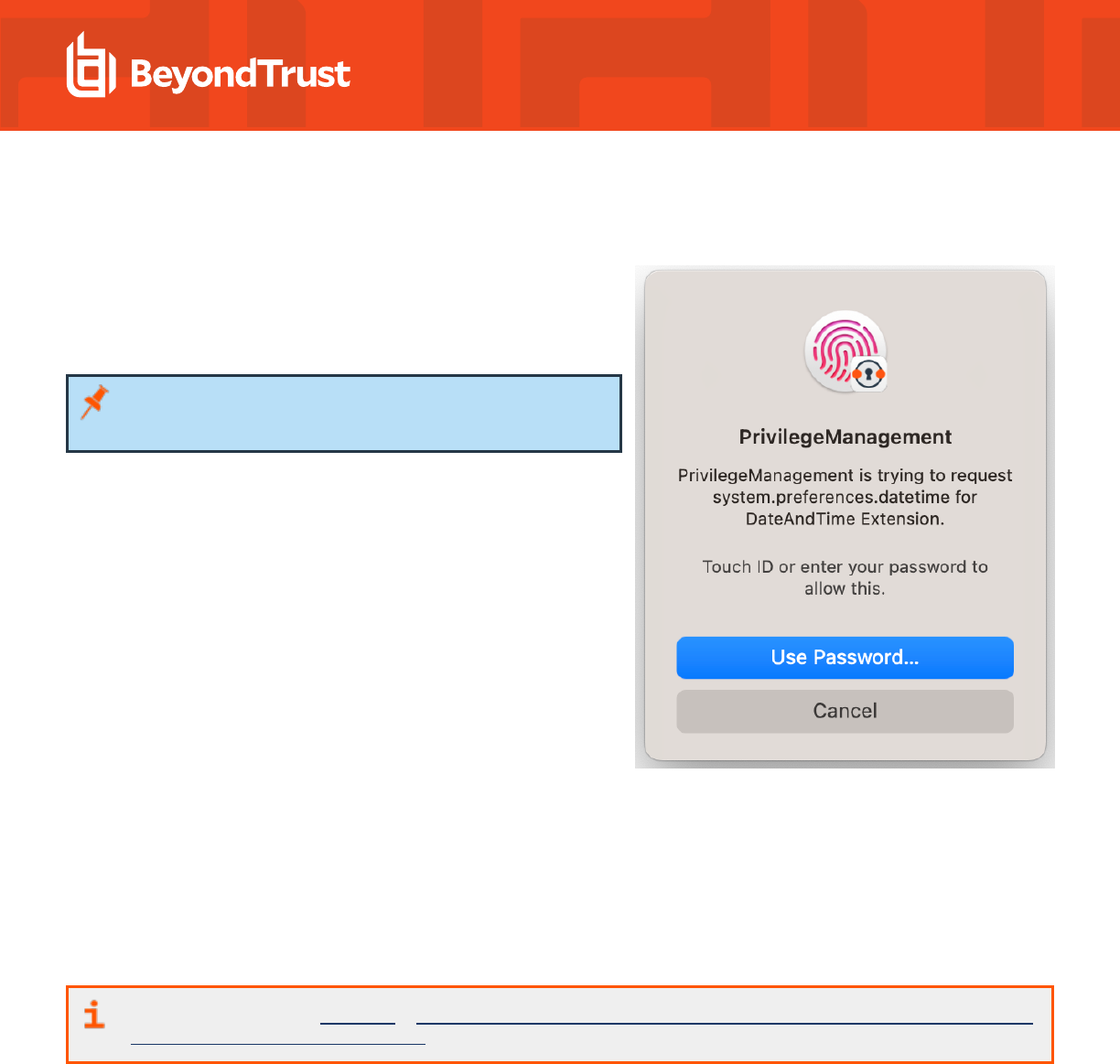
Use Touch ID Authentication with Allow Messages
When an end user activates Touch ID, their fingerprint can be used for
authentication rather than a password. In an Endpoint Privilege
Management for Mac implementation, Touch ID authentication can be used
in place of password authentication on an Endpoint Privilege Management
message dialog box, as shown here.
Note: The PrivilegeManagement text in the dialog boxes is the
name of BeyondTrust software and cannot be changed.
When creating a message, keep the following in mind:
l
An Allow message template must be used.
l
Authentication Method must be set to Password Only or Any.
l
The message cannot be combined with any other message types.
When Touch ID is not activated or available on the user's machine, then the user is presented with a message to enter their password.
Starting in Endpoint Privilege Management 23.1, you can configure Touch ID in the Policy Editor messages as an authentication method.
For more information, see Messages at https://www.beyondtrust.com/docs/privilege-management/console/pm-cloud/use-the-
policy-editor/policy-editor-messages.htm.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
85
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Mac Deployment
Endpoint Privilege Management for Mac settings can be exported from the MMC as a standalone XML configuration file, which can be
distributed to macOS endpoints using your own deployment strategy.
To export the Endpoint Privilege Management for Mac settings to an XML file:
1. Select the Endpoint Privilege Management Settings node.
2. Right-click and select Export.
3. Select an appropriate destination for the exported XML file, ensuring the file is named defendpoint.xml.
Add Endpoint Privilege Management for Mac Settings to a Mac Client
Computer
Endpoint Privilege Management for Mac settings are stored in the file /etc/defendpoint/local.xml, and can be overwritten with an
exported XML file from the MMC. To prevent any invalid permissions being applied, we recommend this file is replaced using the following
command. In this example, the source XML file is located on your Desktop:
sudo cp ~/Desktop/local.xml /etc/defendpoint/local.xml
Endpoint Privilege Management for Mac will apply the new settings immediately, and does not require any restart.
Do not delete the local.xml file as this will interfere with the client machine’s ability to enforce policy. If the local.xml file is deleted from a
client machine, replace the file and restart the machine.
Mac Policy Structure and Precedence
Structure
Policies are stored in /etc/defendpoint/. For example:
l
ic3.xml
l
epo.xml
l
mdm.xml
l
local.xml
l
bi.xml
These policies are not case-sensitive. All policies stored in this location must have the following permissions to ensure policy acceptance
and system security:
l
Ownership of _defendpoint user and group (for example, sudo chown _defendpoint:_defendpoint <policy path>)
l
Permission for the _defendpoint user and group to read the policy, but not other users (for example, sudo chmod 660 <policy
path>
The policy or policies that are read and loaded by the dppolicyserver are dependent on the settings under the config.order in the
defendpoint.plist.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
86
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Note: If all policies are deleted, the local.xml policy is regenerated. The regenerated local.xml policy will not contain any
license or rules.
Precedence
The policy precedence is determined in the defendpoint.plist which is stored in /Library/Application
Support/Avecto/Defendpoint/defendpoint.plist.
The defendpoint.plist is appended or created with the precedence lists (as below) on start up or installation. But editing and saving of the
list is applied immediately.
<key>config.order</key>
<array>
<string>ic3</string>
<string>epo</string>
<string>bi</string>
<string>mdm</string>
<string>local</string>
</array>
You can edit the defendpoint.plist file manually to change the policy precedence if required.
The dppolicyserverd will go through the policies under /etc/defendpoint/ by finding the first policy in the config.order, and if it can't find
a policy of that name, it will progress to the next in the list.
If a policy is found with the correct name it will load it, irrespective of if it has a license.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
87
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Audits and Reports
Endpoint Privilege Management for Mac sends events to the local Application event log, depending on the audit and privilege monitoring
settings within the Endpoint Privilege Management for Mac policy.
Additionally, BeyondTrust also provides an enterprise level, scalable reporting solution in Endpoint Privilege Management Reporting.
Endpoint Privilege Management Reporting includes a rich set of dashboards and reports designed to simplify the centralized management
and auditing of Endpoint Privilege Management for Mac activity throughout the desktop and server estate. Each dashboard provides
detailed and summarized information regarding Application, User, Host, and Workstyle usage.
For more information, please contact BeyondTrust.
Events
The following events are logged by Endpoint Privilege Management for Mac:
Event ID Description
100 Process has started with admin rights added to token.
106 Process has started with no change to the access token (passive mode).
116 Process execution was blocked.
120 Process execution was canceled by the user
130 An application bundle that can be installed into the /Applications folder by a user that is not a member of the
Administrator group.
131 An application bundle that can be deleted from the /Applications folder by a user that is not a member of the
Administrator group.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
88
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Use Smart Card Authentication
If multi-factor authentication (MFA) using smart cards is implemented in your environment, you can configure Endpoint Privilege
Management for Mac to work with your MFA implementation.
Endpoint Privilege Management for Mac supports smart card and Yubikey.
Predeployment Setup
To use Endpoint Privilege Management for Mac with a policy that enforces using smart cards on a local machine, you must configure the
endpoints to allow unmapped users to authenticate using passwords only.
IMPORTANT!
Failure to configure endpoints to allow users to authenticate using passwords only will prevent Endpoint Privilege Management for
Mac from authorizing controlled rights on behalf of the user.
Run the following command on the endpoint. You can run the command manually or run a script distributed by an MDM solution.
If running the command manually, prepend sudo to the line.
defaults write /Library/Preferences/com.apple.security.smartcard allowUnmappedUsers -int 1
Configure Endpoint Privilege Management for Mac Messaging
After your estate is set up to use MFA, and Endpoint Privilege Management for Mac is successfully deployed, you can require users to
enter their smart card PIN for any action which can be controlled by Endpoint Privilege Management for Mac.
MFA with smart card supports the following authorization types:
l
User Must Authorize: The user must authenticate before proceeding.
l
Designated user must authorize: A designated user must authenticate an action. The designated user authorization type
cannot be used with sudo rules.
For more information, see " Authentication and Authorization Settings" on page 77.
For example, to enforce low flexibility users to authenticate using their smart card PIN if they want to install a downloaded application to
/Applications. You can create a message in the Policy Editor and assign a name such as Authorize Application Install (PIN required).
To configure messaging on a policy for MFA:
1. Go to the Message Designer.
2. Set the Authorization Type setting to one of the following: User Must Authorize or Designated user must authorize.
3. Set the Authentication Method setting to Any or Smart card only to enable smart card messages.
4. After you create the message, find your existing application assignment in your Workstyle which prompts the user for installing
application bundles in to /Applications.
5. Select your message from the End User Message setting.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
89
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

MFA Support in Endpoint Privilege Management for Mac sudo Rules
Smart card support can also be implemented in a command line scenario. You can configure an Endpoint Privilege Management for Mac
Workstyle with a sudo command Application Rule. When there is a match on the rule, the user must correctly enter their smart card PIN
before they can proceed.
The high-level overview to set up smart card authentication with a sudo rule:
l
Create your Application Group. Add the application you want to run using sudo.
l
Customize your message in the Message Designer. Be sure to set
the following:
o
Authentication type: User must authorize
o
Authentication Method: Smart card only
l
Create the Application Rule in Workstyles. Set up the Application
Rule and select the message you created.
The following screen capture shows an example where nvim is configured to run with sudo and smart card authentication. Access is only
permitted after the user correctly enters the smart card PIN.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
90
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

ServiceNow User Request Integration
You can configure a new message type in Endpoint Privilege Management that allows end users to raise a request for access to an
application or installer directly in ServiceNow. This ticket can then be reviewed and approved (or denied) in ServiceNow.
On the next check-in from the endpoint to EPM, this exception is automatically applied and the end user is approved to perform their
action. (Or if the Service Desk operator denied the request, the user is not allowed to continue the action).
Typically an endpoint checks in with EPM every 60 minutes, and receives any ticket decisions at this point. If you want to get the update
immediately to the endpoint, you can attempt to launch the application again to get an immediate update of that request.
This integration is supported on the EPM platform only. All configuration occurs in EPM.
For more information, see ServiceNow User Request Integration in the Endpoint Privilege Management Administration Guide,
at https://www.beyondtrust.com/docs/privilege-management/console/pm-cloud/configuration/servicenow-user-request-
integration.htm.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
91
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Logging
Set up Audit Logs
Starting in version 23.1, audit log rotation is introduced to avoid large audit log files.
When the defendpointd process starts, a new log configuration file is created with the settings /var/log/defendpoint/audit.log 644 5
10000 * JN only when there is no configuration set up in the /etc/newsyslog.conf for the audit.log file or when the
com.beyondtrust.audit.conf file doesn't already exist.
If the file com.beyondtrust.audit.conf has the settings mentioned above, the audit log rotates up to 6 archived files every 30 minutes if
the audit.log file is larger than 10000 kilobytes — roughly 10 megabytes.
The archive uses the naming convention as follows:
The archive starts with the audit.log file name. Files following include an index number (0 being the newest and 5 the oldest created).
Each log file name ends with the extension .bz2, which is a bZip2 compression type:
l
audit.log.0.bz2
l
audit.log.1.bz2
l
audit.log.2.bz2
l
audit.log.3.bz2
l
audit.log.4.bz2
l
audit.log.5.bz2
If you are using the CaptureConfig utility, only the first two files are retrieved (audit.log and audit.log.0.bz2).
To set up audit logging:
1. When Endpoint Privilege Management for Mac is installed, it checks to see if the following path and file is present. If it's not, it
creates it: /var/log/defendpoint/audit.log
2. This file cannot be edited during output. If this file is deleted, Endpoint Privilege Management for Mac recreates it dynamically. If
the folder structure is deleted, Endpoint Privilege Management for Mac recreates it when the endpoint is restarted.
3. To view the log file, run the following command in Terminal. By default, Standard users are not permitted to run this sudo
command. You must configure a policy to allow this.
Optionally, you can use the CaptureConfig utility. Please contact BeyondTrust Technical Support to get a copy.
sudo cat /var/log/defendpoint/audit.log
4. The log file is maintained by the core macOS service newsyslog. The newsyslog.conf file contains various log files and
associated settings and is maintained by the core macOS. The newsyslog.conf file is located at /etc/newsyslog.conf.
Note: This part of the set up must be done by a user who can write to this location or by using a mobile device management
(MDM) solution.
5. In the newsyslog.conf file, the settings are outlined and have column headers:
l
logfilename
l
mode
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
92
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

l
count
l
size
l
when
l
flags
6. For the purposes of the maintenance of the audit.log file, you must populate the logfilename, mode, count, size and/or when,
and flags attributes in the newsyslog.conf file.
l
logfilename: Path and filename
l
mode: File mode. For example, settings for read/write for each user type (POSIX file permissions)
l
count: Count for amount of archived files (count starts from 0)
l
size: Threshold for log size in KB
l
when: Threshold for log size in terms of time. For example, new log everyday at X, or every month
l
flag: Instruction for processing the archived/turn-over file. This is most likely to be JN or ZN
An example of a line in the newsyslog.conf for Endpoint Privilege Management for Mac:
/var/log/defendpoint/audit.log 644 5 1000 * JN
This indicates that:
l
The filename is audit.log
l
It can be viewed by all user types but can only be edited by the root user
l
It has an archive count of 5 (6 archived files, not including the current log)
l
It has a threshold of 1MB for turn-over/archiving
l
It doesn't have a date turn over
l
For archiving, files are to be compressed into a bzip file
Note: The threshold relies on the newsyslog service. This service is "low" priority in macOS and only reads the .conf
file approximately every 30mins. Using the example line above, the log can become greater than 1MB prior to the
service reading the newsyslog.conf file due to it being a ‘threshold’ value, rather than each log file being of equal size.
7. After you apply the newsyslog.conf by adding the audit.log line to it, you can run sudo newsyslog -nv in the Terminal to see
the state of the logging, when the next roll over is, and whether there are any syntax issues.
View Unified Logging
Unified logging stores log messages in memory or in a data store. Unified logging is available in macOS 10.12 and later and supersedes
Apple System Logger (ASL).
Prior to macOS 10.12, log messages were written to specific disk locations.
View logs in the Console application or the log command line tool.
To view the debug logs of a process on the endpoint:
1. Open the Console app. By default, debug and info messages are not displayed. You can select an event in the main window to
view the logs for it.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
93
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

2. Click Now in the top left of the tool bar to see new messages in real time.
3. Select Actions > Include Info Messages and Actions > Include Debug Messages to add these to the log.
4. Using the search bar on the top-right, you can enter the name of a process that you want to filter on. For example, defendpointd
for Endpoint Privilege Management for Mac or PMCAdapter for EPM Adapter log messages.
5. You can further manipulate the filter from the search bar or by right-clicking on the process and selecting an additional filter option.
For more information about unified logging, see Logging at https://developer.apple.com/documentation/os/logging.
Obtain Debug Logs from the Endpoint
Unified logging does not store info or debug strings on the hard disk. They are only displayed while the Console application is open.
You must use the log config command to create plist files for each Endpoint Privilege Management for Mac daemon and change the
logging file. These plists are created in the /Library/Preferences/Logging directory.
Note: You can also get debug logs from the endpoint using the CaptureConfig utility. Please contact BeyondTrust Technical
Support to obtain it.
1. To create plists and change the logging level for the Endpoint Privilege Management for Mac daemons, run the following
commands in the terminal:
sudo log config --subsystem com.avecto.defendpointd --mode persist:debug
sudo log config --subsystem com.avecto.custodian --mode persist:debug
sudo log config --subsystem com.avecto.dppolicyserverd --mode persist:debug
sudo log config --subsystem com.avecto.Defendpoint --mode persist:debug
2. Once these commands have been run, you have two options:
l
Obtain a centralized log you can send to BeyondTrust Technical Support. This is the recommended approach.
IMPORTANT!
You would ideally collect the logs into a central log file using the following command, however this logs every process on the endpoint,
not just the Endpoint Privilege Management for Mac processes.
sudo log collect —-last <num><m/h/d>
Note: You must replace the <num> value with an integer and then append m for months, h for hours, or m for minutes
depending on how long it took to replicate the issue. This produces a .logarchive file in the current user's directory.
l
Alternatively, you can create a log for each Endpoint Privilege Management for Mac daemon by using the following
commands. This process outputs .log files in the user's home directory that can be edited or moved as required. As this
information is split across multiple log files, it is not the recommended approach, however it can be used when the first
approach is not viable.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
94
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

log show --predicate 'subsystem == "com.avecto.custodian"' --style json --debug --last 1h >
~/Documents/Custodian.logarchive
log show --predicate 'subsystem == "com.avecto.defendpointd"' --style json --debug --last 1h
> ~/Documents/defendpointd.logarchive
log show --predicate 'subsystem == "com.avecto.dppolicyserverd"' --style json --debug --last
1h > ~/Documents/dppolicyserverd.logarchive
log show --predicate 'subsystem == "com.avecto.Defendpoint"' --style json --debug --last 1h
> ~/Documents/Defendpoint.logarchive
Apply Anonymous Logging to Events
By default, Endpoint Privilege Management for Mac will include user and computer specific information in all audit events. You can set
your Application Rules to not log this information for events associated with your rules by setting the Raise an Event option to On
(Anonymous) on each rule.
You can also set whether user or computer information is kept anonymous for audit events that are not associated with a rule, such as
events raised for having an invalid license.
To enable anonymous auditing for events not associated with a rule, edit the following section in the defendpoint.plist configuration file:
<key>AnonymousLogging</key>
<string>true</string>
To disable anonymous auditing for events not associated with a rule, edit the following section in the defendpoint.plist configuration file:
<key>AnonymousLogging</key>
<string>false</string>
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
95
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Troubleshoot
Check Endpoint Privilege Management for Mac is Installed and Functioning
If you are having problems, the first step is to verify you have installed the client and the client is functioning.
l
Endpoint Privilege Management for Mac: The graphical interface of Endpoint Privilege Management for Mac on the toolbar for
messages and end user interaction
l
defendpointd: The Endpoint Privilege Management for Mac daemon that manages interaction with Endpoint Privilege
Management for Mac
l
dppolicyserverd: Manages policy and communicates with defendpointd
l
Custodian: Manages authentication as required by Endpoint Privilege Management for Mac
Check Settings are Deployed
Assuming Endpoint Privilege Management for Mac is installed and functioning, the next step is to verify you have deployed settings to the
computer or user.
Check Endpoint Privilege Management for Mac is Licensed
One of the most common reasons for Endpoint Privilege Management for Mac not functioning, is the omission of a valid license from the
Endpoint Privilege Management for Mac settings. If you create multiple policies, then you must ensure the computer or user receives at
least one policy containing a valid license. To avoid problems, it is simpler to add a valid license to every set of Endpoint Privilege
Management for Mac settings that you create.
Check Workstyle Precedence
Assuming Endpoint Privilege Management for Mac is functioning and licensed, most other problems are caused by configuration
problems or Workstyle precedence problems.
Once an application matches an Application Group entry in the Application Rules, then processing will not continue for that application.
Therefore, it is vital you order your entries correctly:
l
If you create multiple Workstyles, Workstyles higher in the list have a higher precedence.
l
If you have multiple rules in the Application Rules section of a Workstyle, entries higher in the list have a higher precedence.
Application Rules are applied to applications launched either directly by the user or by a running process.
If you have multiple policies applying to a user, computer, or both, then you should ensure policy precedence rules are not causing the
problem. If multiple policies are applied to a computer or user, then Endpoint Privilege Management for Mac will apply the policies based
on alphanumeric order with the precedence list in defendpoint.plist.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
96
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
Install macOS Updates On Apple Silicon Hardware
This section goes through the following:
l
Apple Changes with Apple Silicon Hardware
l
Apple Recommended Method for Updating macOS Devices
l
User Initiated Software Updates
l
Allow Standard Users to Use the Full macOS Installer vian Endpoint Privilege Management for Mac
Apple Changes with Apple Silicon Hardware
On the Apple Silicon architecture, Apple has introduced a new concept called Volume Ownership. At the time of writing, any user on the
system with a secure token is considered a volume owner by macOS, regardless of whether they are a local administrator.
This change has affected the software update mechanism because updates now require these credentials. This is necessary so that
different volumes on local storage used during the software update process can be unlocked to allow the update data to be written to
them.
For more information, see Use secure token, bootstrap token and volume ownership in deployments at
https://support.apple.com/en-gb/guide/deployment/dep24dbdcf9e/web.
Apple-Recommended Method for Updating macOS Devices
Official guidance from Apple is that organizations managing multiple Mac devices use their MDM provider to manage and schedule OS
updates.
One advantage of managing software updates in this way is that organizations are not beholden to the vigilance of their end users to
ensure that the latest security patches are applied.
For more MDM provider specific guidance, see:
l
For JAMF, macOS Upgrades and Updates Using a Mass Action Command at https://docs.jamf.com/technical-
papers/jamf-pro/deploying-macos-upgrades/10.34.0/macOS_Updates_and_Upgrades_Using_a_Mass_Action_
Command.html
l
For Kandji, Configuring Managed OS for macOS at https://support.kandji.io/support/solutions/articles/72000560360-
configuring-managed-os-for-macos
User-Initiated Software Updates
End users ultimately want to update the macOS version on their hardware, and with Endpoint Privilege Management for Mac installed this
is still possible, although there are some caveats.
Endpoint Privilege Management for Mac does allow policy control to allow standard users to install delta or minor updates through the
System Settings / System Preferences app but not the full installer. The differences are described below.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
97
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Full Installer or Delta Installer
If the update being presented to the user is shown as a 12GB or larger, this implies that the update is going to attempt to download the
macOS full installer package as opposed to a delta update. If an end user is offered only the full installer, the user can quit the System
Preferences application and relaunch it. At that point they are offered the delta installer, which is approximately 6GB. Once this is shown,
they can update the OS. During the user-initiated software update, the end user is prompted for an additional username and password
dialog, which is presented by macOS. Endpoint Privilege Management for Mac does not control this dialog.
End users can update macOS with delta updates without issue and we go through this process below with examples.
End users will encounter issues when using the full-installer, because a user who is both a local administrator and who has a secure token
(volume owner) is required to approve the installation.
Note: Be aware that when applying a delta update on macOS Ventura, for example when upgrading from 13.0 to 13.1, the
username and password dialog box displays that it requires the credentials for an administrative user. For more information,
see "Delta Update Process (Ventura)" on page 99.
This is a bug in macOS and will be fixed in a future release to reflect the same experience from macOS Monterey.
For more information, see "Allow Standard Users to Use the Full macOS Installer via Endpoint Privilege Management for Mac"
on page 101.
Why is the Extra Username and Password Dialog Box Required?
As mentioned above in the Changes with Apple Silicon Hardware section, on the Apple Silicon architecture a new concept is introduced by
Apple called Volume Ownership. At the time of writing, the software update mechanism requires these credentials so that different
volumes on local storage used during the software update process can be unlocked to allow the update data to be written to them.
For more information, see Use secure token, bootstrap token and volume ownership in deployments at
https://support.apple.com/en-gb/guide/deployment/dep24dbdcf9e/web.
Ensure You are Using the Delta Installer
Sometimes when users initially go to the Software Update preference
pane, there is an option to install a macOS update, which indicates a very
large download size (see screenshot). This is a full installer method and is
subject to the problems detailed in the section below regarding the full
macOS installer.
If you see a 12GB update, check back at a later time when there might be a
much smaller download available. It might be necessary to quit the System
Preferences application and reopen it for the smaller update to be offered.
In the case of updating to macOS Ventura 13.1 from macOS Monterey, the
update is approximately 6GB, as opposed to the 12GB full installer.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
98
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Delta Update Process (Ventura)
Screen captures in this section are from macOS Ventura.
When navigating the System Settings app via General > Software Update, you might be presented with an Endpoint Privilege
Management for Mac confirmation dialog box, depending on how you configured your Endpoint Privilege Management for Mac policy.
1. After the Endpoint Privilege Management for Mac message is
approved, click Update Now, and then agree to the Terms and
Conditions dialog box.
2. Enter a username and password. The Software Update dialog box
prompts for an administrator username and password; due to a bug
in macOS, the currently logged-in user must only enter their
username and password. The bug will be resolved in an upcoming
release.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
99
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

3. After authenticating, the install downloads and the update
completes.
Delta Update Process (Monterey)
Screen captures in this section are from macOS Monterey.
1. When you open the Software Update preference pane in macOS
Monterey, you will see something like the screenshot shown. Click
Upgrade Now.
2. Depending on the Endpoint Privilege Management for Mac policy
applied, you might need to approve the operation, as shown here.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
100
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
3. After approving the dialog box, enter your password on the system
dialog box. This does not need to be an administrative user, though
it must be valid credentials for any valid user on the system who has
a secure token.
Allow Standard Users to Use the Full macOS Installer via Endpoint
Privilege Management for Mac
When running a full macOS installer from the /Applications folder (Install macOS xxxx.app) on Apple Silicon (M1 / M1 Pro / M1 Max)
hardware as a standard user, there is an additional prompt for administrator authentication after the initial request for administrator
credentials.
When installing as a standard user with Endpoint Privilege Management for Mac, this causes problems that means the installation cannot
be completed. You might be prompted for the password of user _avectodaemon. This occurs because Endpoint Privilege Management
for Mac does not have access to a secure token within macOS. We encourage customers to remove local administrator privileges for their
users to increase security of the endpoint.
When macOS is installing macOS updates, the credentials of a user with a secure token are required to write data to volumes on local
storage that must first be unlocked.
The full installer expects credentials for a user who is both a local administrator and has a secure token, and does not accommodate
requesting credentials of any secure token enabled user. As such, an install using this method cannot proceed with Endpoint Privilege
Management for Mac installed.
See the following section for a workaround method that allows installation to proceed in cases in which using the full installer is the only
available option.
Note: A similar issue has also been highlighted in the Jamf Community when attempting the update to Monterey via Jamf
scripts. The Jamf community has created a workaround for this issue. For more information, see macOS installer script not
working for Apple Silicon M1 Macbook + macOS Monterey at https://community.jamf.com/t5/jamf-pro/macos-installer-script-
not-working-for-apple-silicon-m1-macbook/m-p/250873/highlight/true#M233793.
The development team has an open ticket with Apple to resolve this issue; the KB article will be updated in due course. If you
want to reach out to Apple directly, please quote ticket "Feedback ID - FB9750688."
Supported Method for Full Installer
The following method can be used to allow users to upgrade to macOS with a full installer without needing to uninstall Endpoint Privilege
Management for Mac or provide the end user with real administrator credentials on the machine. This is possible because the command
line installer accepts the password of the currently logged-in user to gain access to a secure token regardless of local administrator status.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
101
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

1. In your policy editor, find an appropriate application assignment that
will approve authorization requests without displaying a message to
the user. If your policy is based on QuickStart, then Authorize -
General Business Applications is a good fit.
2. Select Authorize - General Business Applications on the left,
and then right-click in the main area and select Sudo Command.
In the wizard, type /Applications/Install macOS Monterey.app, and
then click the Next button.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
102
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

3. Click Next on the Description dialog box (or type a description),
and then click Finish to add the command.
4. Once your new policy is applied to your endpoints, you can run the
installer with the command:
sudo /Applications/Install\ macOS\
Monterey.app/Contents/Resources/startosinstall --
agreetolicense --passprompt
When the password prompt appears, the standard user types their
password to continue.
5. The installer runs and the machine restarts, after which it is updated to macOS Monterey.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
103
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE

Windows and macOS OS Technical Support Statement
At BeyondTrust, we strive to offer technical support for all operating systems (OS), but we acknowledge the limitations that may arise
when using outdated operating systems.
At our sole discretion, we may make commercially reasonable efforts to provide limited technical support for supported EPM (Endpoint
Privilege Management) agents installed on outdated Windows OS or macOS. However, it's essential to note that according to
BeyondTrust’s End of Life Policy, we are not committed to providing any security, functional, or operational code fixes for agents installed
on unsupported or outdated OS versions.
We highly recommend keeping your operating systems up-to-date to ensure the security, stability, and optimal performance of your
systems and applications. Running outdated OS versions may expose your organization to various security risks and vulnerabilities, as
they may lack essential security patches and updates provided by the OS vendor.
In the event that you encounter issues with EPM agents installed on outdated Windows OS or macOS, BeyondTrust will make every effort
to provide guidance and assistance within the constraints of our End of Life Policy.
We remain committed to supporting our customers in their cybersecurity efforts and are here to assist you in navigating any challenges
you may encounter. If you have any questions or require further assistance regarding technical support for EPM agents, please don't
hesitate to contact our support team.
SALES: www.beyondtrust.com/contact
SUPPORT: www.beyondtrust.com/support
DOCUMENTATION: www.beyondtrust.com/docs
104
©2003-2024 BeyondTrust Corporation. All Rights Reserved. Other trademarks identified on this page are owned by their respective owners. BeyondTrust is not a chartered bank or trust company, or
depository institution. It is not authorized to accept deposits or trust accounts and is not licensed or regulated by any state or federal banking authority.
TC: 6/28/2024
ENDPOINT PRIVILEGE MANAGEMENT FOR MAC
24.4 ADMINISTRATION GUIDE
